13 Managing SecInfo¶
The SecInfo management provides centralized access to a wide range of information technology (IT) security information including the following categories:
- Vulnerability Tests (VT)
VTs test the target system for potential vulnerabilities.
- Common Vulnerabilities and Exposures (CVE)
CVEs are vulnerabilities published by vendors and security researchers.
- Common Platform Enumeration (CPE)
CPE offers standardized names for products used in the IT.
- CERT-Bund Advisories
CERT-Bund Advisories are published by the CERT-Bund, the Computer Emergency Response Team of the German Federal Office for Information Security (BSI) (German: Bundesamt für Sicherheit in der Informationstechnik, abbreviated as BSI). The main task of the CERT-Bund is the operation of a warning and information service publishing information regarding new vulnerabilities and security risks as well as threats for IT systems.
- DFN-CERT Advisories
DFN-CERT advisories are published by the DFN-CERT [German only], the Computer Emergency Response Team of the German National Research and Education Network (German: Deutsches Forschungsnetz, abbreviated as DFN).
CVEs and CPEs are published and made accessible by the National Institute of Standards and Technology (NIST) as part of the National Vulnerability Database (NVD) (see Chapter 13.2).
Note
Greenbone is also offering all SecInfo data online, accessible via the SecInfo portal. The SecInfo portal provides all SecInfo described in the following chapters and the CVSS calculator.
Access to the SecInfo Portal is provided by activating a guest access (see Chapter 8.1.4).
13.1 Vulnerability Tests (VT)¶
VTs are test routines used by the appliance. They are part of the Greenbone Enterprise Feed which is updated regularly. VTs include information about development date, affected systems, impact of vulnerabilities and remediation.
List Page
All existing VTs can be displayed by selecting SecInfo > NVTs in the menu bar.
For all VTs the following information is displayed:
- Name
Name of the VT.
- Family
Family of VTs to which the VT belongs.
- Created
Date and time of creation.
- Modified
Date and time of last modification.
- CVE
CVE that is checked for using the VT.
- Solution Type

Type of measure to remedy the vulnerability. The following solution types exist:
 Vendor fix: Information is available about an official fix that is issued by the original vendor of the affected product.
Unless otherwise noted, it is assumed that this fix fully resolves the vulnerability.
Vendor fix: Information is available about an official fix that is issued by the original vendor of the affected product.
Unless otherwise noted, it is assumed that this fix fully resolves the vulnerability. Workaround: Information about a configuration or specific deployment scenario that can be used to avoid exposure to the vulnerability is available.
This is usually the “first line of defense” against a new vulnerability before a mitigation or vendor fix has been issued or even discovered.
Workaround: Information about a configuration or specific deployment scenario that can be used to avoid exposure to the vulnerability is available.
This is usually the “first line of defense” against a new vulnerability before a mitigation or vendor fix has been issued or even discovered. Mitigation: Information about a configuration or specific deployment scenario that helps to reduce the risk of the vulnerability is available but that does not resolve the vulnerability on the affected product.
Mitigation: Information about a configuration or specific deployment scenario that helps to reduce the risk of the vulnerability is available but that does not resolve the vulnerability on the affected product. Will not fix: There is no fix for the vulnerability and there never will be one.
This is often the case when a product has been orphaned, is no longer maintained or otherwise deprecated.
Information should contain details about why there will be no fix issued.
Will not fix: There is no fix for the vulnerability and there never will be one.
This is often the case when a product has been orphaned, is no longer maintained or otherwise deprecated.
Information should contain details about why there will be no fix issued. None: Currently there is no fix available.
Information should contain details about why there is no fix.
None: Currently there is no fix available.
Information should contain details about why there is no fix.
- Severity
Qualitative measure of a vulnerability’s severity according to the Common Vulnerability Scoring System (CVSS) (see Chapter 13.2.3). This includes a severity score, which is a number from 0.0 to 10.0, with 10.0 being the most severe, and a severity class based on the score:
High: 7.0–10.0
Medium: 4.0–6.9
Low: 0.1–3.9
Log: 0.0
- QoD
Short for “Quality of Detection”. The QoD describes the reliability of the executed vulnerability detection. It is a value between 0 % and 100 %, with 100 % being the most reliable.
By default, only results that were detected by VTs with a QoD of 70 % or higher are displayed. The filter can be adjusted to show results with a lower QoD (see Chapter 7.3.1).
For more information see Chapter 10.2.6.
Note
By clicking  below the list of VTs more than one VT can be exported at a time. The drop-down list is used to select which VTs are exported.
below the list of VTs more than one VT can be exported at a time. The drop-down list is used to select which VTs are exported.
Details Page
Click on the name of a VT to display the details of the VT. Click  to open the details page of the VT.
to open the details page of the VT.
The following actions are available in the upper left corner:
13.2 Security Content Automation Protocol (SCAP)¶
The National Institute of Standards and Technology (NIST) provides the National Vulnerability Database (NVD). The NVD is a data repository for the vulnerability management of the US government. The goal is the standardized provision of the data for automated processing. By that, vulnerability management is supported and the implementation of compliance guidelines is verified.
The NVD provides different databases including the following:
Checklists
Vulnerabilities
Misconfigurations
Products
Threat metrics
The NVD utilizes the Security Content Automation Protocol (SCAP). SCAP is a combination of different interoperable standards. Many standards were developed or derived from public discussion.
The public participation of the community in the development is an important aspect for accepting and spreading SCAP standards. SCAP is currently specified in version 1.3 and includes the following components:
- Languages
XCCDF: Extensible Configuration Checklist Description Format
OVAL: Open Vulnerability and Assessment Language
OCIL: Open Checklist Interactive Language
Asset Identification
ARF: Asset Reporting Format
- Collections
CCE: Common Configuration Enumeration
CPE: Common Platform Enumeration
CVE: Common Vulnerabilities and Exposure
- Metrics
CVSS: Common Vulnerability Scoring System
CCSS: Common Configuration Scoring System
- Integrity
TMSAD: Trust Model for Security Automation Data
OVAL, CCE, CPE and CVE are trademarks of NIST.
The Greenbone Enterprise Appliance uses CVE, CPE and CVSS. By utilizing these standards, the interoperability with other systems is guaranteed. The standards also allow comparing the results.
Vulnerability assessment systems such as the Greenbone Enterprise Appliance can be validated by NIST respectively. The appliance has been validated with respect to SCAP version 1.0.
13.2.1 CVE¶
In order to avoid multiple naming of the same vulnerability by different organizations and to ensure a uniform naming convention, MITRE founded the Common Vulnerabilities and Exposure (CVE) program. Every vulnerability is assigned a unique identifier, consisting of the release year and a simple number, and serves as a central reference.
CVEs are published and made accessible by the National Institute of Standards and Technology (NIST) in the National Vulnerability Database (NVD). The NVD complements the CVEs with information regarding the elimination, severity, potential impact and affected products of the vulnerability.
Greenbone refers to the NVD and the appliance combines the CVE information, VTs and CERT-Bund/DFN-CERT advisories.
List Page
All existing CVEs can be displayed by selecting SecInfo > CVEs in the menu bar.
Note
The availability of a CVE on the appliance depends on its availability in the NVD. As soon as it has been published there, it takes 1–2 working days for it to appear in the SecInfo.
Columns like Severity may display N/A for one of the following reasons:
The CVE was published but no vulnerability analysis/severity assessment was carried out by the NVD yet. This can take a few days up to a few weeks.
Such CVEs can be identified when inspecting the corresponding NVD entry. As long as not available is displayed for the severity, N/A is shown for the severity on the appliance.
There is always a delay of 1–2 working days between the vulnerability analysis/severity assessment and the time the updated information is displayed in the SecInfo management.
The availability of a CVE on the appliance does not mean that it is also covered by a VT.
To determine whether a specific CVE is covered, the filter cve=<CVE-ID> can be used on the NVTs page (see Chapter 13.1).
The column CVSS Base Vector shows the CVSS vector used for calculating the severity of a CVE. This vector includes the CVSS version defined for the CVE.
By clicking on the vector, the page CVSSv2/CVSSv3/CVSSv4 (Base) Score Calculator is opened. The fields of the corresponding calculator are already filled in, depending on which CVSS version is used to calculate the severity of the CVE (see Chapter 13.2.3).
Note
By clicking  below the list of CVEs more than one CVE can be exported at a time. The drop-down list is used to select which CVEs are exported.
below the list of CVEs more than one CVE can be exported at a time. The drop-down list is used to select which CVEs are exported.
Details Page
Click on the name of a CVE to display the details of the CVE. Click  to open the details page of the CVE (see Fig. 13.1).
to open the details page of the CVE (see Fig. 13.1).
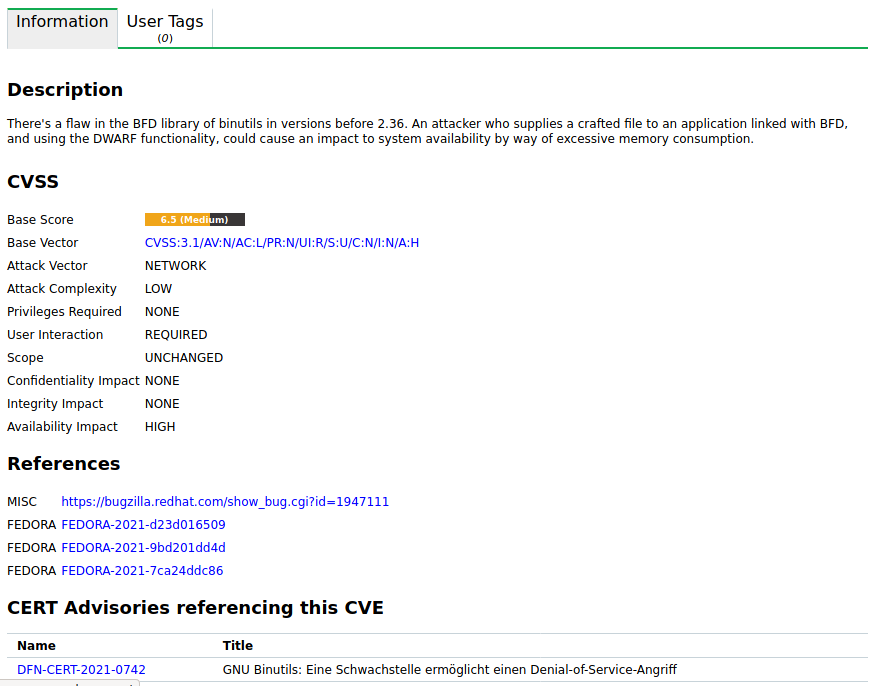
Fig. 13.1 Details page of a CVE¶
The following registers are available:
- Information
General information about the CVE.
- User Tags
Assigned tags (see Chapter 7.4).
The following actions are available in the upper left corner:
13.2.2 CPE¶
Common Platform Enumeration (CPE) is a structured naming scheme for information technology systems, platforms and packages. Based on the generic syntax for Uniform Resource Identifiers (URI), CPE includes a formal name format, a language for describing complex platforms, a method for checking names against a system and a description format for binding text and tests to a name.
CPEs are published and made accessible by the National Institute of Standards and Technology (NIST) in the National Vulnerability Database (NVD).
A CPE name starts with “cpe:/”, followed by up to seven components separated by colons (see Fig. 13.2).
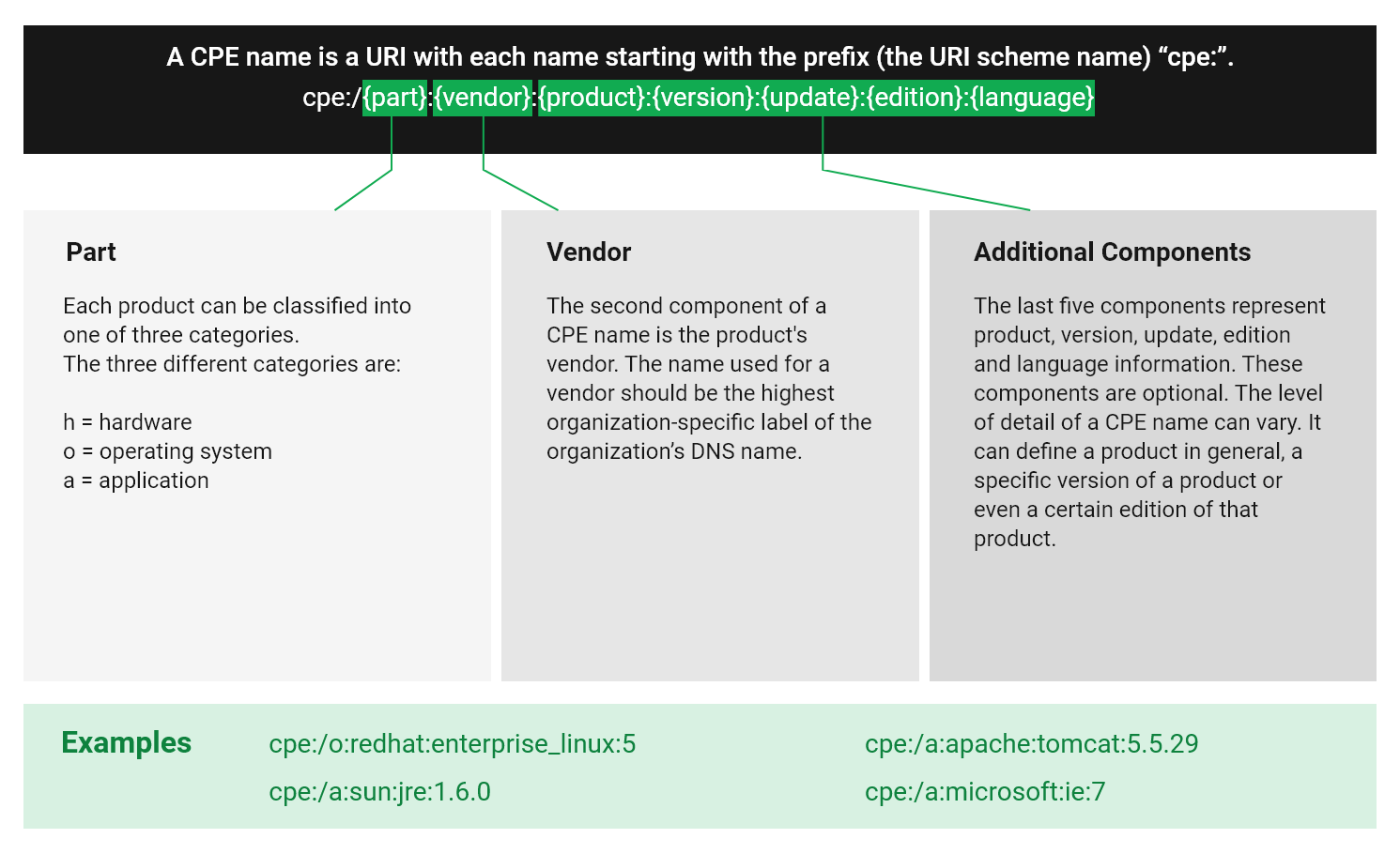
Fig. 13.2 Name structure of a CPE name¶
The combination of CPE and CVE standards enables the conclusion of existing vulnerabilities when discovering a platform or product.
List Page
All existing CPEs can be displayed by selecting SecInfo > CPEs in the menu bar.
Note
The availability of a CPE on the appliance depends on its availability in the NVD. As soon as it has been published there, it takes 1–2 working days for it to appear in the SecInfo.
Note
By clicking  below the list of CPEs more than one CPE can be exported at a time. The drop-down list is used to select which CPEs are exported.
below the list of CPEs more than one CPE can be exported at a time. The drop-down list is used to select which CPEs are exported.
Details Page
Click on the name of a CPE to display the details of the CPE. Click  to open the details page of the CPE.
to open the details page of the CPE.
The following registers are available:
- Information
General information about the CPE.
- User Tags
Assigned tags (see Chapter 7.4).
The following actions are available in the upper left corner:
13.2.3 CVSS¶
To support the interpretation of a vulnerability, the Common Vulnerability Scoring System (CVSS) was invented. The CVSS is an industry standard for describing the severity of security risks in computer systems.
Security risks are rated and compared using different criteria. This allows for the creation of a priority list of countermeasures.
The CVSS is developed by the CVSS Special Interest Group (CVSS-SIG) of the Forum of Incident Response and Security Teams (FIRST). The current CVSS score version is 4.0.
GOS 22.04 supports CVSS v3.0/v3.1. The extent of the CVSS v3.0/v3.1 support depends on the Greenbone Enterprise Feed. However, VTs and CVEs may contain CVSS v2 and/or CVSS v3.0/v3.1 data.
If a VT/CVE contains both CVSS v2 data and CVSS v3.0/v3.1 data, the CVSS v3.0/v3.1 data is always used and shown.
The CVSS Base Vector shown in the details preview and on the details page of a VT can be v2, v3.0 or v3.1.
The CVSS Base Vector shown in the table on the page CVEs can be v2, v3.0 or v3.1. Clicking on the CVSS base vector opens the page CVSSv2/CVSSv3/CVSSv4 (Base) Score Calculator. The input boxes of the corresponding calculator are already pre-filled.
The CVSS score supports base score metrics, temporal score metrics, and environmental score metrics.
- Base score metrics
Base score metrics test the exploitability of a vulnerability and their impact on the target system. Access, complexity and requirement of authentication are rated. Additionally, they rate whether the confidentiality, integrity or availability is threatened.
- Temporal score metrics
Temporal score metrics test whether a completed example code exists, the vendor already supplied a patch and confirmed the vulnerability. The score will be changing drastically in the course of time.
- Environmental score metrics
Environmental score metrics describe the effect of a vulnerability within an organization. They take damage, target distribution, confidentiality, integrity and availability into account. This assessment strongly depends on the environment in which the vulnerable product is used.
Since the base score metrics are merely meaningful in general and can be determined permanently, the appliance provides them as part of the SecInfo data.
The CVSS calculator can be opened by selecting Help > CVSS Calculator in the menu bar (see Fig. 13.3). The calculator for CVSS version 2.0, the calculator for CVSS version 3.0/3.1 and the calculator for CVSS version 4.0 are displayed.
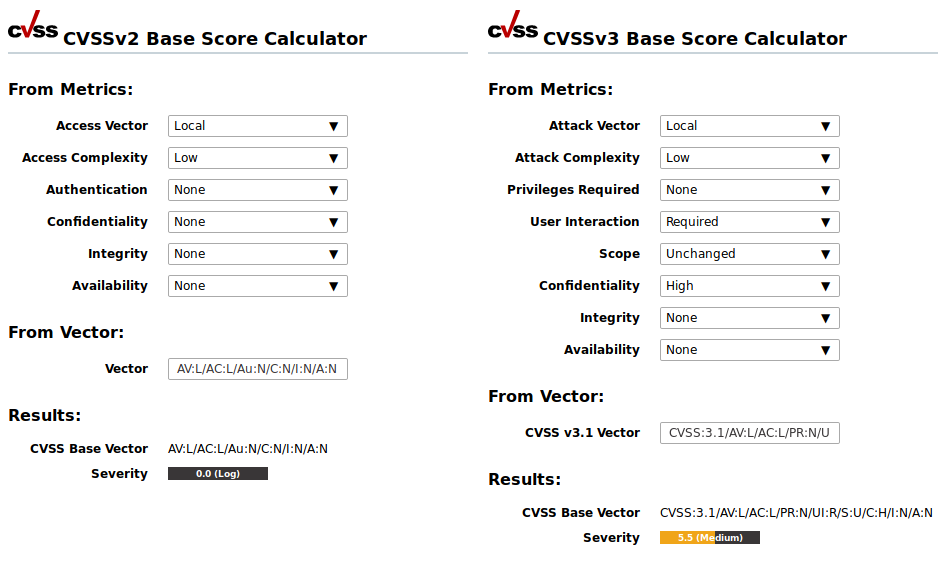
Fig. 13.3 CVSS calculator for calculating severity scores¶
13.2.3.1 CVSS Version 2.0¶
The following formula is used by the CVSS calculator for version 2.0:
BaseScore = roundTo1Decimal( ( ( 0.6 * Impact ) +
( 0.4 * Exploitability ) - 1.5 ) * f( Impact ) )
“Impact” is calculated as follows:
Impact = 10.41 * (1 - (1 - ConfImpact) *
(1 - IntegImpact) * (1 - AvailImpact))
“Exploitability” is calculated as follows:
Exploitability = 20 * AccessVector * AccessComplexity * Authentication
Note
The function f( Impact ) is 0, if the impact is 0.
In all other cases the value is 1.176.
The other values are constants:
- Access Vector
Requires local access: 0.395
Adjacent network accessible: 0.646
Network accessible: 1.0
- Access Complexity
High: 0.35
Medium: 0.61
Low: 0.71
- Authentication
Requires multiple instances of authentication: 0.45
Requires single instance of authentication: 0.56
Requires no authentication: 0.704
- ConfImpact
None: 0.0
Partial: 0.275
Complete: 0.660
- IntegImpact
None: 0.0
Partial: 0.275
Complete: 0.660
- AvailImpact
None: 0.0
Partial: 0.275
Complete: 0.660
13.2.3.2 CVSS Version 3.0/3.1¶
The following formula is used by the CVSS calculator for version 3.0/3.1:
* If Impact <= 0, BaseScore = 0
* If Scope is "Unchanged":
BaseScore = Roundup (Minimum ((Impact + Exploitability), 10))
* If Scope is "Changed":
BaseScore = Roundup (Minimum (1.08 * (Impact + Exploitability), 10))
“ISS” (Impact Sub-Score) is calculated as follows:
ISS = 1 - ((1 - Confidentiality) * (1 - Integrity) * (1 - Availability))
“Impact” is calculated as follows:
* If Scope is "Unchanged":
Impact = 6.42 * ISS
* If Scope is "Changed":
Impact = 7.52 * (ISS - 0.029) - 3.25 * (ISS - 0.02)¹⁵
“Exploitability” is calculated as follows:
Exploitability = 8.22 * Attack Vector * Attack Complexity
* Privileges Required * User Interaction
The other values are constants:
- Attack Vector
Network: 0.85
Adjacent: 0.62
Local: 0.55
Physical: 0.2
- Attack Complexity
Low: 0.77
High: 0.44
- Privileges Required
None: 0.85
Low: 0.62 (or 0.68 if Scope is “Changed”)
High: 0.27 (or 0.5 if Scope is “Changed”)
- User Interaction
None: 0.85
Required: 0.62
- Confidentiality
None: 0.0
Low: 0.22
High: 0.56
- Integrity
None: 0.0
Low: 0.22
High: 0.56
- Availability
None: 0.0
Low: 0.22
High: 0.56
13.2.3.3 CVSS Version 4.0¶
Note
CVSS 4.0 is not yet supported beyond the CVSS calculator. It will be supported in a future major GOS version.
The calculation used by the CVSS calculator for version 4.0 is described in this documentation.
13.3 CERT-Bund Advisories¶
The CERT-Bund, the Computer Emergency Response Team of the German Federal Office for Information Security (BSI), is the central point of contact for preventive and reactive measures regarding security related computer incidents.
With the intention of avoiding harm and limiting potential damage, the work of CERT-Bund includes the following:
Creating and publishing recommendations for preventive measures
Pointing out vulnerabilities in hardware and software products
Proposing measures to address known vulnerabilities
Supporting public agencies efforts to respond to IT security incidents
Recommending various mitigation measures
Working closely with the National IT Situation Centre and the National IT Crisis Response Centre
The services of CERT-Bund are primarily available to federal authorities and include the following:
24 hour on call duty in cooperation with the IT Situation Centre
Analyzing incoming incident reports
Creating recommendations derived from incidents
Supporting federal authorities during IT security incidents
Operating a warning and information service
Active alerting of the federal administration in case of imminent danger
The CERT-Bund offers a warning and information service (German: Warn- und Informationsdienst, abbreviated as “WID”). Currently this service offers two different types of information:
- Advisories
This information service is only available to federal agencies as a closed list. The advisories describe current information about security critical incidents in computer systems and detailed measures to remediate security risks.
- Short Information
Short information features the short description of current information regarding security risks and vulnerabilities. This information is not always verified and could be incomplete or even inaccurate.
The Greenbone Enterprise Feed contains the CERT-Bund Short Information. Both the information in the old format [German only] (up to June 2022) and the information in the new format [German only] (from June 2022) are included.
There are very minor differences in the advisory metadata between both formats. The formats can be used interchangeably for all use cases.
Information of the old format follow the scheme
CB-KYY/ID, for exampleCB-K22/0704.Information of the new format follow the scheme
WID-SEC-YYYY-ID, for exampleWID-SEC-2022-0311.
List Page
All existing CERT-Bund advisories can be displayed by selecting SecInfo > CERT-Bund Advisories in the menu bar.
The severity displayed for a CERT-Bund advisory is not taken directly from the advisory. Instead, it is the highest severity among all CVEs referenced in the advisory. If no CVEs are references in the CERT-Bund advisory, N/A is shown for its severity. For more information about CVEs and the severity shown for them, see Chapters 13.2.1 and 13.2.3.
Note
By clicking  below the list of CERT-Bund advisories more than one CERT-Bund advisory can be exported at a time. The drop-down list is used to select which CERT-Bund advisories are exported.
below the list of CERT-Bund advisories more than one CERT-Bund advisory can be exported at a time. The drop-down list is used to select which CERT-Bund advisories are exported.
Details Page
Click on the name of a CERT-Bund advisory to display the details of the CERT-Bund advisory. Click  to open the details page of the CERT-Bund advisory.
to open the details page of the CERT-Bund advisory.
The following registers are available:
- Information
General information about the CERT-Bund advisory.
- User Tags
Assigned tags (see Chapter 7.4).
The following actions are available in the upper left corner:
13.4 DFN-CERT Advisories¶
While the individual VTs, CVEs and CPEs are created primarily to be processed by computer systems, the DFN-CERT [German only] publishes new advisories regularly.
The DFN-CERT is responsible for hundreds of universities and research institutions that are associated with the German Research and Education Network (German: Deutsches Forschungsnetz, abbreviated as DFN). Additionally, it provides key security services to government and industry.
An advisory describes especially critical security risks that require fast reacting. The DFN-CERT advisory service includes the categorization, distribution and rating of advisories issued by different software vendors and distributors. Advisories are obtained by the Greenbone Enterprise Appliance and stored in the database for reference.
List Page
All existing DFN-CERT advisories can be displayed by selecting SecInfo > DFN-CERT Advisories in the menu bar.
The severity displayed for a DFN-CERT advisory is not taken directly from the advisory. Instead, it is the highest severity among all CVEs referenced in the advisory. If no CVEs are references in the DFN-CERT advisory, N/A is shown for its severity. For more information about CVEs and the severity shown for them, see Chapters 13.2.1 and 13.2.3.
Note
By clicking  below the list of DFN-CERT advisories more than one DFN-CERT advisory can be exported at a time. The drop-down list is used to select which DFN-CERT advisories are exported.
below the list of DFN-CERT advisories more than one DFN-CERT advisory can be exported at a time. The drop-down list is used to select which DFN-CERT advisories are exported.
Details Page
Click on the name of a DFN-CERT advisory to display the details of the DFN-CERT advisory. Click  to open the details page of the DFN-CERT advisory.
to open the details page of the DFN-CERT advisory.
The following registers are available:
- Information
General information about the DFN-CERT advisory.
- User Tags
Assigned tags (see Chapter 7.4).
The following actions are available in the upper left corner: