1 Introduction¶
1.1 Vulnerability Management¶
In IT security, the combination of three elements influence the attack surface of an IT infrastructure:
Cyber criminals with sufficient experience, equipment and money to carry out the attack.
Access to the IT infrastructure.
Vulnerabilities in IT systems, caused by errors in applications and operating systems, or incorrect configurations.
If these three elements come together, a successful attack on the IT infrastructure is likely.
Since most vulnerabilities are known and can be fixed, the attack surface can be actively influenced using vulnerability management. Vulnerability management involves looking at the IT infrastructure from the outside – just as potential cyber criminals would. The goal is to find every vulnerability that could exist in the IT infrastructure.
Vulnerability management identifies weaknesses in the IT infrastructure, assesses their risk potential, and recommends concrete measures for remediation. In this way, attacks can be prevented through targeted precautionary measures. This process – from recognition to remedy and monitoring – is carried out continuously.
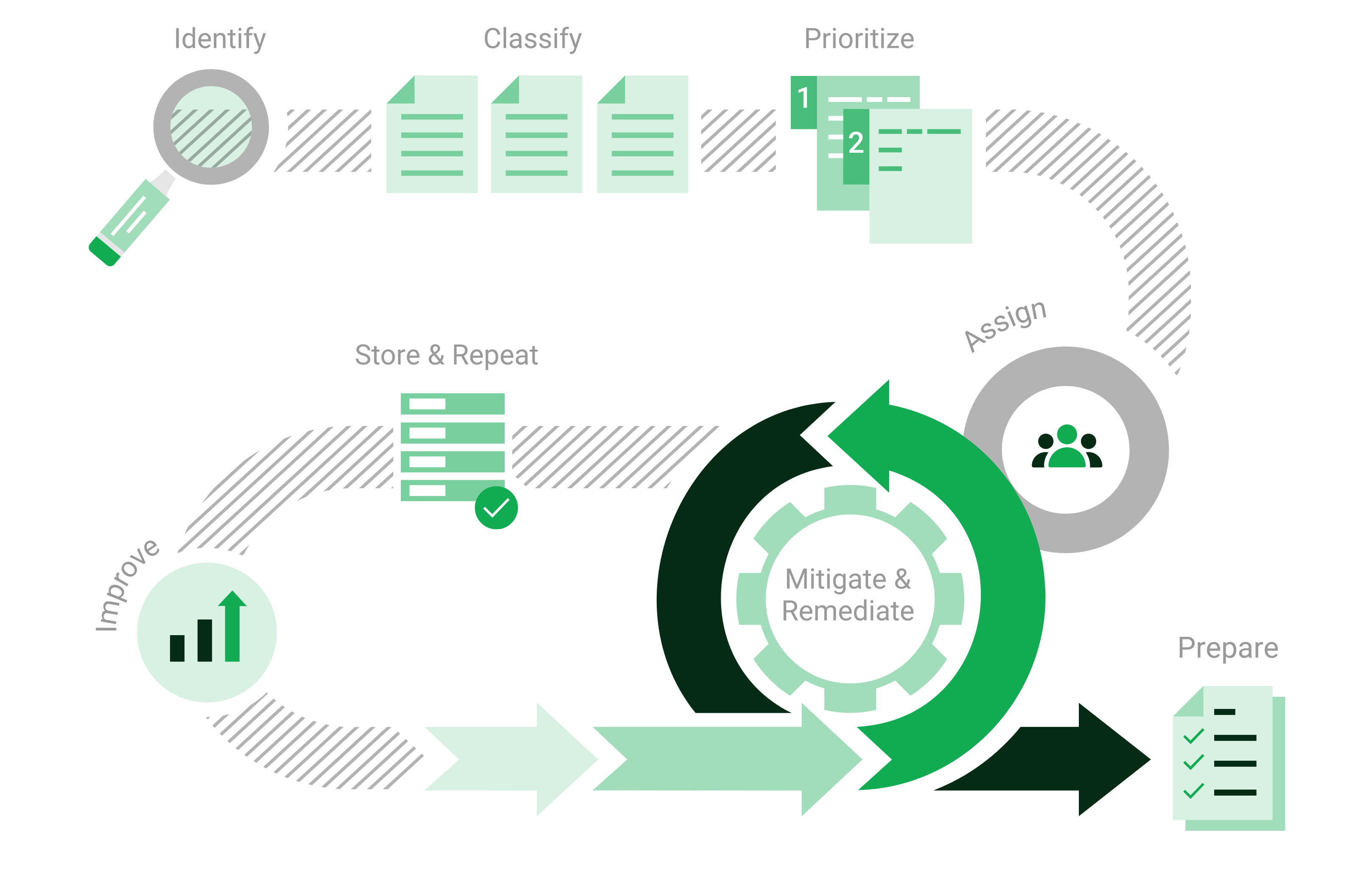
Fig. 1.1 Process of vulnerability management¶
1.2 Greenbone Enterprise Appliance¶
The Greenbone Enterprise Appliance is a vulnerability management appliance, available as hardware and virtual models. It assists companies and agencies with automated and integrated vulnerability assessment and management.
1.2.1 Components and Field of Application¶
The appliance consists of the Greenbone Operating System (GOS) on which the Greenbone Enterprise Feed is installed, a scan service, the web interface and, in case of a physical appliance, a special hardware. The feed provides the vulnerability tests (VTs) that the scan service uses to detect existing vulnerabilities on the inspected network.
As new vulnerabilities are discovered every day, new vulnerability tests must be added constantly. Greenbone analyzes CVE [1] messages and security advisories of vendors and develops new vulnerability tests. The feed is updated daily and thus always provides the latest vulnerability tests to reliably detect the newest vulnerabilities.
The appliance is flexible in use and can be utilized for large enterprises, for medium-sized and small companies as well as for special use cases like audits and trainings. Due to the master-sensor technology, the appliance can also be deployed in high-security sectors.
1.2.2 Types of Scans¶
The appliance discovers vulnerabilities through different perspectives of cyber criminals:
- External
The appliance can simulate an external attack to identify outdated or misconfigured firewalls.
- Demilitarized Zone (DMZ)
The appliance can identify actual vulnerabilities that may be exploited by cyber criminals who get past the firewall.
- Internal
The appliance can also identify exploitable vulnerabilities in the internal network, for example those targeted by social engineering or computer worms. Due to the potential impact of such attacks, this perspective is particularly important for the security of any IT infrastructure.
DMZ and internal scans can be both unauthenticated and authenticated. When performing an authenticated scan, the appliance uses credentials and can discover vulnerabilities in applications that are not running as a service but have a high risk potential (for example, web browsers, office applications or PDF viewers).
- Information about web application scanning
The vulnerability scanner of the Greenbone Enterprise Appliance scans hosts, specified by a domain name or an IP address. A website URL, however, consists of more parts than just a domain name or an IP address. Since the appliance’s scanner does not process the other parts of a URL, it cannot automatically analyze and test the structure of a website. It is therefore not a Web Application Security Scanner (WASS) or an HTTP scanner.
However, if a host is scanned on which a web application is running, and if both a known vulnerability exists and a suitable vulnerability test for it is included in the feed, the appliance may still detect the vulnerability.
1.2.3 Vulnerability Classification and Elimination¶
The detected vulnerabilities are rated according to their severity using the Common Vulnerability Scoring System (CVSS). The severity can be used to determine which vulnerabilities to prioritize when executing remediation measures. The most important measures are those that protect the system against critical risks and eliminate the corresponding vulnerabilities.
Fundamentally, there are two options to deal with vulnerabilities:
Eliminating the vulnerability by updating the software, removing the vulnerable component or changing the configuration.
Implementing a rule in a firewall or in an intrusion prevention system (virtual patching).
Virtual patching is the apparent elimination of the vulnerability through a compensating control. The real vulnerability still exists and the cyber criminals can still exploit the vulnerability if the compensating control fails or if an alternate approach is used.
An actual patch or update of the affected software is always preferred over virtual patching.
Footnotes