6 Upgrading the Greenbone Enterprise Appliance to the Latest Version¶
GOS 20.08 provides seamless upgrades to the new major version GOS 21.04.
All system settings and user data are retained and automatically migrated to the new version unless a change in default behavior affects a specific setting or data. For a list of changes to the default behavior, see Chapter 6.5.
6.1 Upgrading the Greenbone Operating System¶
Note
Before upgrading to GOS 21.04, some requirements must be met in GOS 20.08:
- The latest version of GOS 20.08 must be installed on the appliance.
- The sensor type of all configured sensors must be changed to OSP using the menu option Migrate all sensors to OSP as described here.
- A Feed Import Owner must be set as described here.
- The data objects must be installed. For this, a feed update is required after setting the Feed Import Owner.
Note
For Greenbone Enterprise 5300/6400:
Depending on how old these appliances are, they may run with SATA mode “IDE”. If this is the case, GOS 21.04 may not boot until the SATA mode is updated.
The SATA mode can be changed as described in Chapter 6.5.4.2.
The upgrade to GOS 21.04 can be carried out as follows:
Select Maintenance and press Enter.
Select Upgrade and press Enter.
Select Switch Release and press Enter.
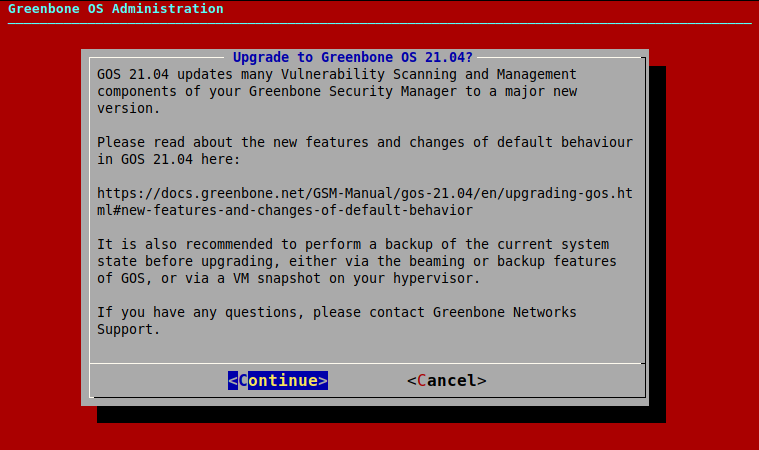
→ A warning informs that the appliance is upgraded to a major new version (see Fig. 6.1).
Select Continue and press Enter.
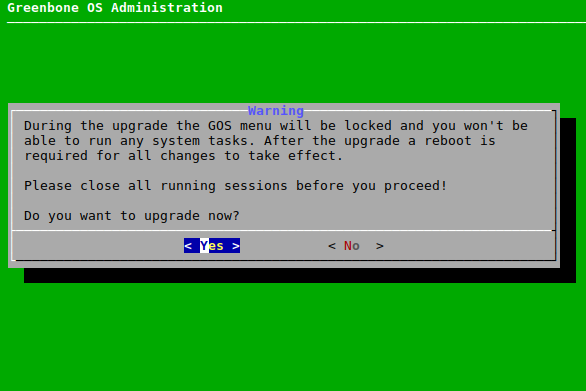
→ A warning informs that the appliance is locked during the upgrade to GOS 21.04 (see Fig. 6.2).
Note
No system operations can be run during the upgrade and all running system operations must be closed before upgrading.
Select Yes and press Enter.
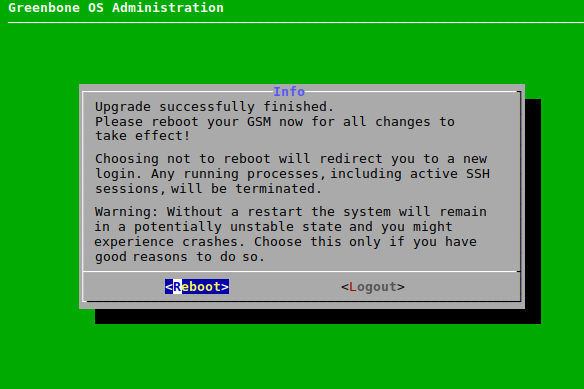
→ A message informs that the upgrade was started.
Note
When the upgrade is finished, a message informs that a reboot is required to apply all changes (see Fig. 6.3).
Select Reboot and press Enter.
→ After the reboot is finished, it is checked if there are any unfinished setup steps. If there are unfinished steps, a message asks whether they should be completed now.
6.2 Upgrading the Flash Partition to the Latest Version¶
The internal flash partition of the appliance contains a backup copy of GOS and is used in case of a factory reset.
Upgrading the GOS version stored on the flash partition is recommended (see Chapter 7.3.8).
6.4 Reloading the Web Interface After an Upgrade¶
After an upgrade from one major version to another, the cache of the browser used for the web interface must be emptied. Clearing the browser cache can be done in the options of the used browser.
Alternatively, the page cache of every page of the web interface can be emptied by pressing Ctrl and F5.
Note
Clearing the page cache must be done for every single page.
Clearing the browser cache is global and applies to all pages.
6.5 New Features and Changes of Default Behavior¶
The following list displays the major additions and changes of default behavior from GOS 20.08 to GOS 21.04.
Depending on the currently used features, these changes may affect the currently deployed setup. For a full list of changes, see the Roadmap & Lifecycle page.
6.5.1 Reports¶
With GOS 21.04, two new report format are introduced: Vulnerability Report PDF and Vulnerability Report HTML.
The new report formats are modern and clear in appearance and structure. They contain information about all vulnerabilities found.
Note
The new report formats are distributed via the Greenbone Enterprise Feed.
To obtain the latest version of the report formats, a feed update may be required before or after upgrading to GOS 21.04 (see Chapter 7.3.6).
6.5.2 CVSS¶
With GOS 21.04, CVSS v3.0/v3.1 is supported. The extent of the CVSS v3.0/v3.1 support depends on the Greenbone Enterprise Feed.
However, VTs and CVEs may contain CVSS v2 and/or CVSS v3.0/v3.1 data. If a VT/CVE contains both CVSS v2 data and CVSS v3.0/v3.1 data, the CVSS v3.0/v3.1 data is always used and shown.
The page CVSS Calculator now contains both a calculator for CVSS v2 and a calculator for CVSS v3.0/v3.1.
The CVSS Base Vector shown in the details preview and on the details page of a VT can now be v2, v3.0 or v3.1.
The table on the page CVEs now contains the entries Name, Description, Published, CVSS Base Vector and Severity. The CVSS Base Vector can be v2, v3.0 or v3.1. Clicking on the CVSS base vector opens the page CVSS Calculator. The input boxes of the corresponding calculator are already pre-filled.
6.5.3 Boreas Alive Scanner¶
The Boreas alive scanner is a host alive scanner that identifies the active hosts in a target network. It was introduced with GOS 20.08, but was still optional. With GOS 21.04, the Boreas alive scanner is made default.
In comparison to the port scanner Nmap that was traditionally used, the Boreas alive scanner is not limited regarding the maximum number of concurrently performed alive status scans and thus, faster. It is especially suitable for large network ranges with only a small number of active hosts.
Since the Boreas alive scanner is now enabled by default, the settings of the VT Ping Host in the VT family Port scanners are no longer valid.
6.5.4 Hardware Appliances¶
6.5.4.1 New Hardware Models for Midrange Class¶
With GOS 21.04, a new generation of Midrange hardware appliances is introduced.
The new hardware now uses SSD-type hard drives instead of HDDs, which are 10 times faster and also quieter and lighter. There is also more hard drive space available. The RAM type is now DDR4 instead of DDR3, which makes the RAM much faster due to a higher clock rate (3200 MHz). There is also twice to four times as much RAM available. Additionally, a new, faster CPU of the latest generation has been installed.
Additionally, the ports of the appliances changed from 6 ports GbE-Base-TX and 2 ports 1 GbE SFP to 8 ports GbE-Base-TX and 2 ports 10 GbE SFP+.
The product names remain as they are.
6.5.4.2 Preparation for Upgrading a Greenbone Enterprise 5300/6400¶
When upgrading a Greenbone Enterprise 5300 or Greenbone Enterprise 6400 to GOS 21.04, an additional preparation may be necessary.
Depending on how old these appliances are, they may run with SATA mode “IDE”. If this is the case, GOS 21.04 may not boot. The SATA mode has to be changed to “AHCI”.
The SATA mode can be changed in the BIOS. To enter the BIOS, press Delete repeatedly while rebooting or powering on the appliance. In the tab Advanced, select SATA Configuration and change the SATA mode to AHCI Mode.
6.5.5 Virtual Appliances¶
The officially supported hypervisors for the virtual appliances are changed with GOS 21.04.
The Greenbone Enterprise EXA/PETA/TERA/DECA and 25V can be used with Microsoft Hyper-V, VMware vSphere Hypervisor (ESXi) and Huawei FusionCompute.
The Greenbone Enterprise CENO can be used with Microsoft Hyper-V and VMware vSphere Hypervisor (ESXi).
The Greenbone Enterprise ONE can be used with Oracle VirtualBox, VMware Workstation Pro and VMware Workstation Player.
Additionally, GOS 21.04 supports the ARM instruction set on Huawei FusionCompute.
Only hypervisor versions that are still supported by their vendors (i.e., they are not end-of-life) are supported by Greenbone.
6.5.6 Scanning Through a VPN¶
With GOS 21.04, OpenVPN is integrated in GOS to enable scanning through a Virtual Private Network (VPN). This feature is only available on virtual appliances of the Midrange Class. The VPN feature allows for targets that are reachable via the VPN tunnel to be scanned, but has no effect on other targets, network settings, or master-sensor connections.
The VPN connection is configured and established via the GOS administration menu using the IP address of the VPN and a PKCS#12 file containing the necessary certificate authority, certificate, and private key files.
6.5.7 HTTPS¶
With GOS 21.04, the nginx web server is used in addition to the Greenbone Security Assistant Daemon (gsad). nginx uses OpenSSL instead of GnuTLS for defining the available ciphers and protocols of the server.
Operating the web interface is only possible with TLS versions 1.2 or 1.3. For the configuration of the TLS version, the GOS administration menu contains a new menu under Setup > Services > HTTPS > Protocols. There the selection of TLSv1.2, TLSv1.3 or both at the same time is possible. By default, both options are selected. In this case, the web browser selects the version according to its configuration.
The menu under Setup > Services > HTTPS > Ciphers is only displayed if TLS version 1.2 is selected (either alone or in combination with version 1.3). The ciphers are now configured with a different string and the TLS version can no longer be configured using the string.
If only TLS version 1.3 is selected, the cipher suites cannot be configured and the default value of OpenSSL is used instead.
If non-default HTTPS ciphers were configured in GOS 20.08, the ciphers can be reconfigured directly after upgrading to GOS 21.04. In this case, the same dialogs as in Setup > Services > HTTPS > Protocols and Setup > Services > HTTPS > Ciphers are displayed one after the other. If only TLSv1.3 is chosen in the Protocols dialog, the Ciphers dialog is not shown.
If the ciphers are not reconfigured, the default protocol and cipher settings of GOS 21.04 are used.
Additionally, some new menus were added in the GOS administration menu. The menus under Setup > Services > HTTPS > Certificate > Generate and Setup > Services > HTTPS > Certificate > CSR allow the configuration of a Subject Alternative Name (SAN). The menus under Setup > Services > HTTPS > HTTP STS, Setup > Services > HTTPS > OCSP Stapling and Setup > Services > HTTPS > DH Parameters allow the configuration for HTTP Strict Transport Security, OCSP stapling and Diffie-Hellman parameters.
6.5.8 Sensors¶
With GOS 21.04, the Greenbone Management Protocol (GMP) is no longer used to control a sensor appliance via a master appliance. All sensors now use the Open Scanner Protocol (OSP) as the controlling protocol.
In GOS, the sensor type GMP Sensor is retired. On the web interface, the scanner type GMP Scanner is retired. The sensor type that must be used is Greenbone Sensor.
This leads to the sensors being light-weighted and avoids the need for additional credentials on the sensor.
6.5.9 Network Backend¶
With GOS 21.04, the network configuration backend in GOS is improved. This prevents loss of connectivity in specific network setups as well as connection issues with SSH sessions.
The appliance no longer needs to be restarted after specific network settings have been changed.
The networking mode can be updated to the new mode gnm (GOS Network Manager) directly after upgrading to GOS 21.04. If the networking mode is not updated directly after upgrading, it can be changed in the new menu under Setup > Network > Switch Networking Mode.
6.5.10 Web Interface¶
6.5.10.1 Auto False Positives¶
With GOS 21.04, the Auto-FP function is retired.
Old filters with autofp= will remain untouched during migration but have no effect anymore.
6.5.10.2 Severity Class Scheme¶
With GOS 21.04, the selection of alternative severity class schemes (BSI Vulnerability Traffic Light and PCI-DSS) is removed from the user settings. There is now only the NVD Vulnerabiltiy Severity Ratings scheme to determine severity classes based on the severity.
During migration, any selection other than the default will fall back to the default.
6.5.10.3 Simultaneous Scanning via Multiple IP Addresses¶
Some devices – especially IoT devices – may crash when scanned via several IP addresses at the same time. For example, this can happen if the device is connected via IPv4 and IPv6.
With GOS 21.04, it is possible to avoid scanning via several IP addresses at the same time using the new setting Allow simultaneous scanning via multiple IPs when creating a target.
The default of this setting is Yes and reflects the behavior of previous GOS releases.
6.5.10.4 Elevated SSH Privileges¶
With GOS 21.04, it is possible to store credentials for elevated privileges, e.g., root, when creating a target.
6.5.10.5 Report Formats¶
With GOS 21.04, the setting Default Report Format was removed from the user settings.
6.5.11 Greenbone Management Protocol (GMP)¶
The Greenbone Management Protocol (GMP) has been updated to version 21.04 and the API has been adjusted slightly. The usage of some commands has changed and several commands, elements and attributes have been deprecated. The complete reference guide and the list of changes are available here.
6.5.12 SSH¶
With GOS 21.04, the supported key exchange methods for connections to the appliance with an SSH client have been changed. Only the following methods are supported:
- ecdh-sha2-nistp256
- ecdh-sha2-nistp384
- ecdh-sha2-nistp521
- curve25519-sha256
- curve25519-sha256@libssh.org

 English |
English |