7 Managing the Greenbone Operating System¶
Note
This chapter documents all possible menu options.
However, not all appliance models support all of these menu options. Check the tables in Chapter 3 to see whether a specific feature is available for the used appliance model.
7.1 General Information¶
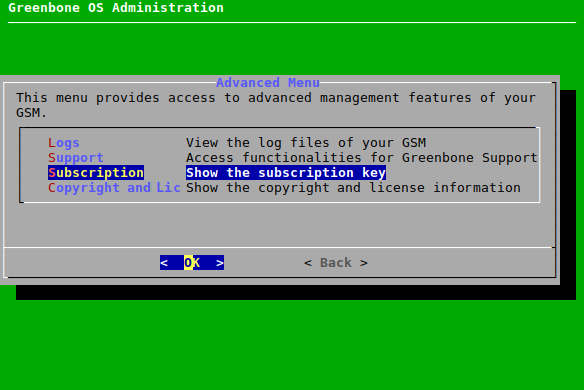
7.1.1 Greenbone Enterprise Feed Subscription Key¶
When purchasing a Greenbone Enterprise Appliance, a unique Greenbone Enterprise Feed subscription key is pre-installed to grant the appliance access to the Greenbone Update Service, also called the Greenbone Feed Service. The subscription key is used for authorization purposes only, not for billing or encryption.
The subscription key is individual for each appliance and cannot be installed on more than one appliance.
If the subscription key is compromised (e.g., gets into the hands of third parties), no damage will occur for the rightful owner of the subscription key. Greenbone will deactivate the compromised key, preventing further unauthorized use. A replacement subscription key may be issued at no cost.
A factory reset will delete the subscription key from the appliance and the key has to be re-installed. If a factory reset is planned, contact the Greenbone Enterprise Support to receive a copy of the subscription key.
7.1.2 Authorization Concept¶
The appliance offers two different levels of access:
- Web Interface/GMP – User Level
- The user level is available via the web interface or the Greenbone Management Protocol (GMP).
- GOS Administration Menu – System Level
- The system level is only available via console or secure shell protocol (SSH).
7.1.2.1 User-Level Access¶
The user level provides access to the vulnerability scanning and vulnerability management functionalities and supports the administration of users, groups and detailed permissions.
Accessing the user level is possible either via the web interface, also called Greenbone Security Assistant (GSA), or via Greenbone Management Protocol (GMP).
Note
For the appliance models Greenbone Enterprise 35 and Greenbone Enterprise 25V, no user-level access is supported. These appliances have to be managed using a master appliance.
When the appliance is delivered by Greenbone or after a factory reset, no user-level account is configured on it. It is necessary to create at least one such account via the system level.
7.1.2.2 System Level Access¶
The system level provides access to the administration of the Greenbone Operating System (GOS). Only a single system administrator account is supported. The system administrator cannot modify system files directly but can instruct the system to change configurations.
GOS is managed using a menu-based graphical interface (GOS administration menu). The system administrator is not required to use the command line (shell) for configuration or maintenance tasks. Shell access is provided for support and troubleshooting purposes only.
Accessing the system level requires either console access (serial, hypervisor or monitor/keyboard) or a connection via SSH. To use SSH, a network connection is required and the SSH service has to be enabled (see Chapter 7.2.4.4).
When the appliance is delivered by Greenbone or after a factory reset, a default system administrator account and password is pre-configured. During the initial setup the system administrator password should be changed (see Chapter 7.2.1.1).
7.1.2.2.1 Accessing the GOS Administration Menu Using the Console¶
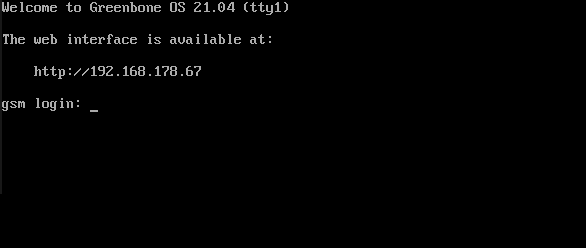
Once turned on, the appliance boots. The boot process can be monitored via the console.
After the boot process is completed, the login prompt is shown (see Fig. 7.1). The default login information is:
User:
adminPassword:
adminNote
During the first setup, this password should be changed (see Chapter 7.2.1.1).
When the appliance is delivered by Greenbone or after a factory reset, a setup wizard is shown after the login to assist with the basic configuration of GOS. By selecting Yes and pressing Enter all mandatory settings can be configured. By selecting No or Cancel and pressing Enter the setup wizard is closed.
7.1.2.2.2 Accessing the GOS Administration Menu Using SSH¶
Note
When the appliance is delivered by Greenbone or after a factory reset, SSH access may be deactivated and has to be enabled first using the console (see Chapter 7.2.4.4). A network connection is required for SSH as well (see Chapter 7.2.2.4).
To establish a SSH connection on Linux, macOS or Unix-like systems, the command line can be used as follows:
$ ssh admin@<appliance>
Replace <appliance> with the appliance’s IP address or domain name.
The host key can be verified by displaying its fingerprint as follows:
Start the GOS administration menu.
Select Setup and press Enter.
Select Services and press Enter.
Select SSH and press Enter.
Select Fingerprint and press Enter.
→ The fingerprint is displayed on the GOS administration menu.
To establish an SSH connection on Microsoft Windows systems, the tools PuTTY or smarTTY can be used. On Microsoft Windows Server 2019, Microsoft Windows 10 Build 1809, or newer, the OpenSSH Client component can be installed to access SSH via the command line.
7.1.3 Using the GOS Administration Menu¶
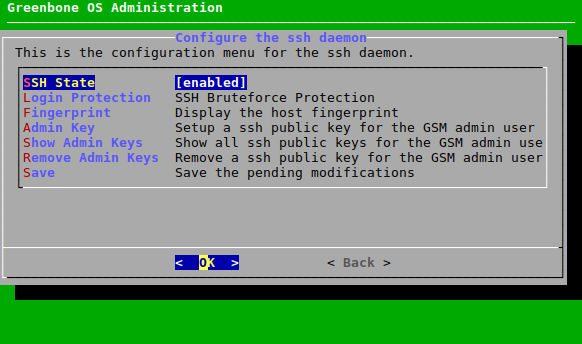
The GOS administration menu can be navigated using a keyboard. The arrow keys of the keyboard can be used to move the current menu selection. Pressing Enter is used to confirm the current menu selection and to continue. Pressing Space is used to toggle on/off switches. The current menu can be exited by pressing Esc.
Configuration changes made in the GOS administration menu are not activated immediately. Instead, the menu option Save is added below the other options (see Fig. 7.2). The changes take effect by selecting Save and pressing Enter.
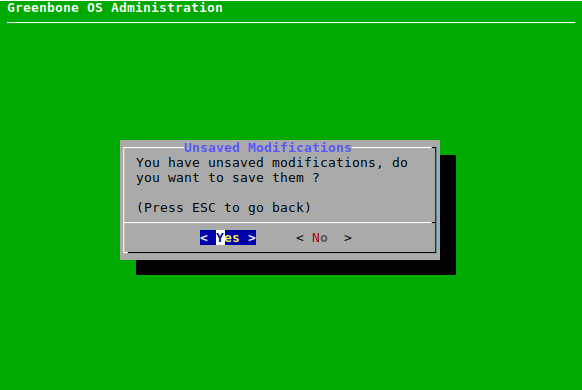
If a menu is exited without saving the outstanding changes, a warning is displayed (see Fig. 7.3). The changes can be saved by selecting Yes and pressing Enter. If No is selected, the changes are discarded.
7.2 Setup Menu¶
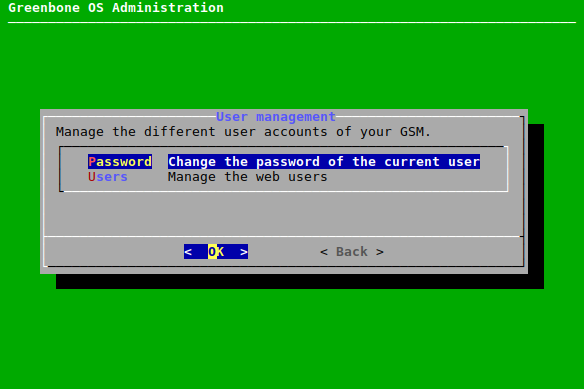
7.2.1 Managing Users¶
The GOS administration menu offers the possibility to manage web users. Web users are the users of the appliance’s web interface.
7.2.1.1 Changing the System Administrator Password¶
The password of the system administrator can be changed. This is especially important during the first base configuration. The factory setting is not suitable for a production environment. The password can be changed as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Password and press Enter (see Fig. 7.4).
Enter the current password and press Enter (see Fig. 7.5).
Enter the new password and press Enter.
Note
Trivial passwords are rejected. This includes the default password
adminas well.Repeat the new password and press Enter.
Note
The change is effective immediately and a commit of the change is not required. A rollback is not possible either.
7.2.1.2 Managing Web Users¶
Note
There are no web users for the appliance models Greenbone Enterprise 35 and Greenbone Enterprise 25V.
For these appliance models, this chapter is not relevant.
To be able to use the appliance, a web administrator must be set up. This user is being referred to as scan administrator in some documentation and by some applications.
The set-up of the first web administrator is only possible using the GOS administration menu as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
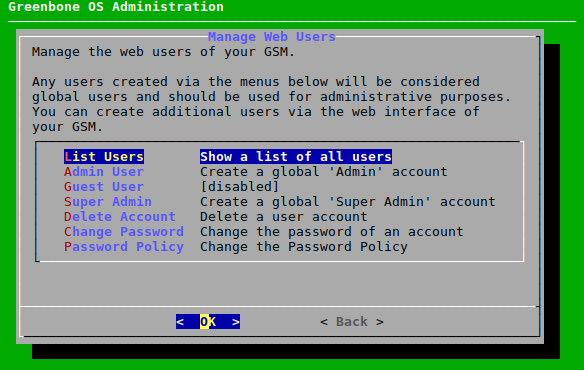
→ Several new options are displayed (see Fig. 7.6).
Select List Users and press Enter to display a list of all configured web users.
Note
More than one user with administrative rights can be set up.
To edit the existing users, or add users with fewer permissions, the web interface has to be used.
7.2.1.3 Creating a Web Administrator¶
A web administrator can be created as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
Select Admin User and press Enter.
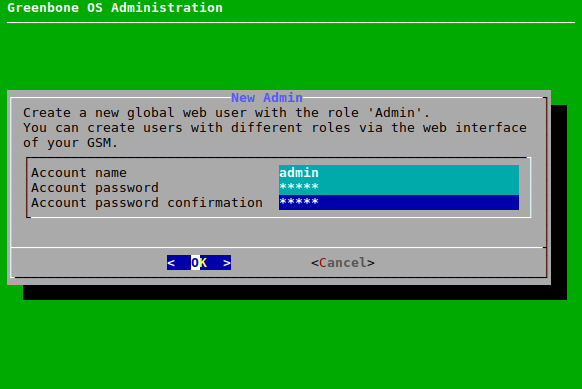
Determine the user name and the password of the web administrator and press Tab (see Fig. 7.7).
Press Enter.
→ The web administrator is created and can be edited in the web interface.
7.2.1.4 Enabling a Guest User¶
To allow a guest to log in without needing a password, this feature has to be activated as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
Select Guest User and press Enter.
Enter the user name and the password of an existing user and press Tab.
Press Enter.
→ The guest user is enabled and can log in to the web interface without needing the password (see Fig. 7.8).
7.2.1.5 Creating a Super Administrator¶
A super administrator can be created as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
Select Super Admin and press Enter.
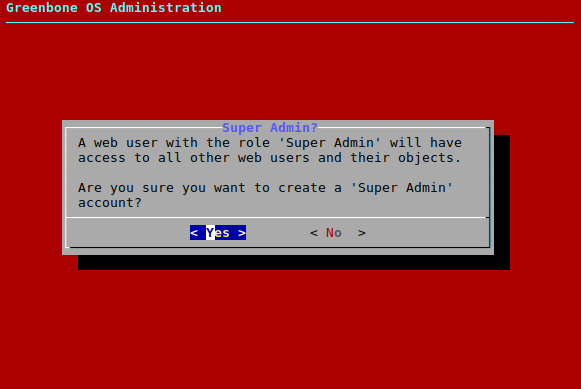
→ A warning asks to confirm the process (see Fig. 7.9).
Select Yes and press Enter.
Determine the user name and the password of the super administrator and press Tab.
Press Enter.
→ The super administrator is created and can be edited in the web interface.
Note
The super administrator can only be edited by the super administrator.
7.2.1.6 Deleting a User Account¶
Note
Super administrators can only be deleted as described here. Deleting a super administrator using the web interface is not possible.
A web user can be deleted as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
Select Delete Account and press Enter.
Select the web user that should be deleted and press Enter.
→ A message asks whether an inheritor should be chosen.
If an inheritor should be selected, select Yes and press Enter.
Select the web user that should be the inheritor and press Enter.
Note
The web user is deleted immediately.
Note
The user who is Feed Import Owner cannot be deleted. Another Feed Import Owner has to be set or the setting has to be unset first (see Chapter 7.2.1.9.1)
Press Enter to return to the previous menu.
7.2.1.7 Changing a User Password¶
The password of a web user can be changed as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
Select Change Password and press Enter.
Select the web user of which the password should be changed and press Enter.
Enter the new password twice and press Tab (see Fig. 7.10).
Press Enter.
7.2.1.8 Changing the Password Policy¶
The requirements for passwords can be changed as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
Select Password Policy and press Enter.
Select Length and press Enter to set the minimal length a password must have.
Note
The minimum length must be at least 10 characters.
Select Username and press Enter to determine whether user name and password can be the same.
Select Complex and press Enter to determine whether a password has to contain at least one letter, one number and one symbol.
7.2.1.9 Configuring the Settings for Data Objects¶
Scan configurations, compliance policies, report formats and port lists by Greenbone (hereafter referred to as “objects”) are distributed via the feed. These objects must be owned by a user, the Feed Import Owner.
The objects are downloaded and updated during a feed update, if a Feed Import Owner has been set.
Only the Feed Import Owner, a super administrator and users who obtained respective rights are able to delete objects. If objects are deleted, they will be downloaded again during the next feed update.
Note
If the objects remain in the trashcan, they do not count as deleted yet and are not downloaded anew during the next feed update.
If no objects should be downloaded, the Feed Import Owner must be unset.
The Feed Import Owner, a super administrator (default role) and an administrator (default role) who currently has permissions for the objects may also grant additional permissions for the objects to other users (see Chapter 9.4.1.1 or 9.4.1.2). Normally, this only applies to the default roles. Custom roles have to be granted permissions manually first.
7.2.1.9.1 Changing the Feed Import Owner¶
The Feed Import Owner is set during the first setup of the appliance (see Chapters 6 and 5). However, the Feed Import Owner can be changed at a later time.
Note
If the Feed Import Owner is changed, the next time the objects are imported from the feed, they will be owned by the new Feed Import Owner, as well as the associated permissions for the configured roles. The previous Feed Import Owner will still own the objects until then.
If the previous Feed Import Owner removes the objects, they will be imported during the feed update, and ownership will be given to the new Feed Import Owner.
The Feed Import Owner can be changed as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
Select Distributed Data and press Enter (see Fig. 7.12).
Select Import Owner and press Enter.
Select the user that should be Feed Import Owner and press Space.
Press Enter.
Note
The user who is Feed Import Owner cannot be deleted (see Chapter 7.2.1.6). Another Feed Import Owner or (Unset) has to be selected.
7.2.1.9.2 Setting the Access Roles¶
By default, the roles User, Admin and Super Admin have read access to the objects, i.e., they can see and use them on the web interface.
However, the roles that should have read access to the objects can be selected as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Users and press Enter.
Select Distributed Data and press Enter.
Select Access Roles and press Enter.
Select the roles that should be able to see and use the data objects and press Space (see Fig. 7.13).
Press Enter.
7.2.2 Configuring the Network Settings¶
7.2.2.1 Updating the Networking Mode to gnm¶
After upgrading from GOS 20.08 to GOS 21.04 (see Chapter 6), a message is displayed, offering to switch to the new network mode gnm (GOS Network Manager).
If the networking mode is not updated directly after upgrading to GOS 21.04, it can be changed as follows:
Select Setup and press Enter.
Select Network and press Enter.
Select Switch Networking Mode and press Enter.
→ A message asks to confirm the change.
Press Enter.
→ A message informs that the networking mode has been updated.
Press Enter to close the message.
Note
After the networking mode is updated, the menu option Switch Networking Mode is no longer available.
7.2.2.2 General Information About Namespaces¶
Some appliance models (Greenbone Enterprise 5400/6500 and Greenbone Enterprise 400/450/600/650) have their network interfaces organized in different namespaces:
- Namespace: Management
- This namespace includes all interfaces required for management activities.
- Namespace: Scan1
- This namespace includes all interfaces required for scanning purposes.
By default, all interfaces are in the management namespace. This enables both management and scan traffic on all interfaces. As soon as at least one interface is in the scan namespace, namespace separation goes into effect.
Only interfaces in the management namespace can handle management traffic. This includes accessing the GOS administration menu, the web interface, the Greenbone Feed Server and configuring the master-sensor communication.
Interfaces in the scan namespace only handle scan traffic.
The namespaces are separated to connect only the interfaces in the scan namespace to networks accessible from the internet. In that way, attacks from the internet cannot reach the management interfaces of the appliance.
Tip
Separating the namespaces is recommended.
7.2.2.3 Switching an Interface to Another Namespace¶
Interfaces that should be moved to another namespace can be selected as follows:
Select Setup and press Enter.
Select Network and press Enter.
Select Configure Namespaces and press Enter.
Press Enter.
Note
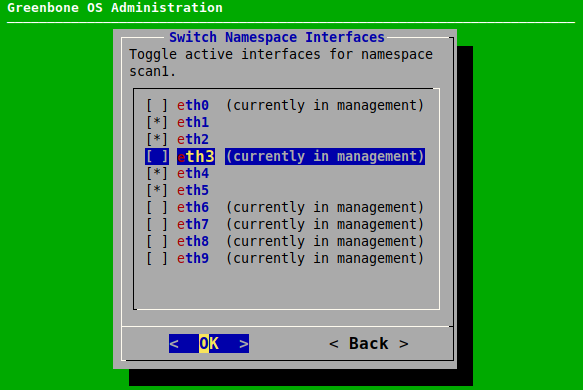
Interfaces in the scan namespace are marked with * (see Fig. 7.14).
Interfaces in the management namespace are labeled accordingly.
Select the interface that should be moved and and press Space.
Note
Not all interfaces may be moved to the scan namespace, otherwise the appliance is no longer accessible.
Press Enter.
7.2.2.4 Configuring Network Interfaces¶
Note
At least one network interface must be configured to access the appliance using the network. Usually the first network adapter eth0 is used for this. The administrator has to configure this network interface and to attach the appliance to the network.
On all virtual appliances, the first network interface is preconfigured with IPv4 via DHCP.
Network interfaces can be configured as follows:
Select Setup and press Enter.
Select Network and press Enter.
Select the namespace of the desired interface and press Enter.
Select Interfaces and press Enter.
Select the desired interface and press Enter.
Note
If there is only one interface in this namespace, the configuration of the interface is opened directly.
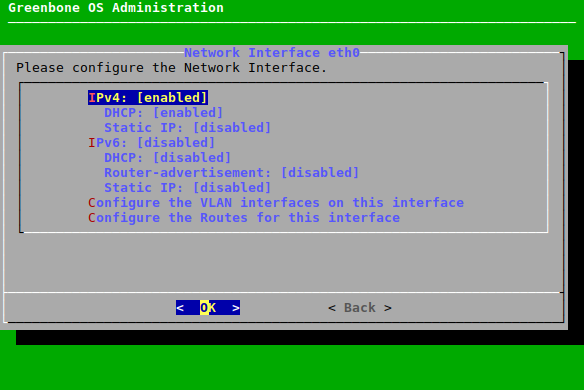
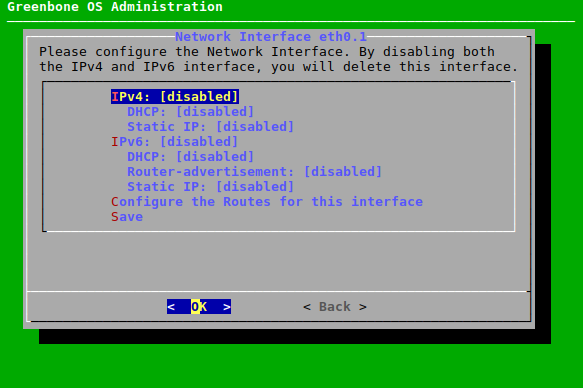
→ The interface can be configured (see Fig. 7.15).
7.2.2.4.1 Setting up a Static IP Address¶
Select the desired interface (see Chapter 7.2.2.4).
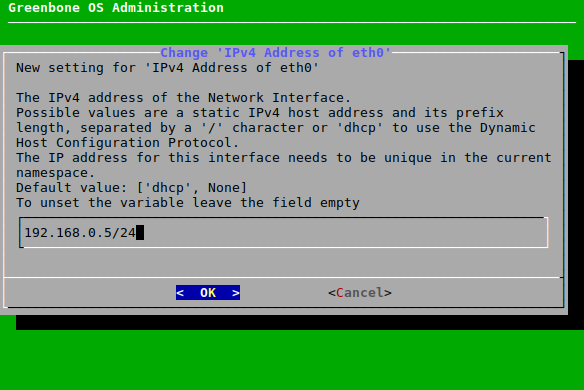
Select Static IP (for IPv4 or IPv6) and press Enter.
Delete
dhcpfrom the input box and replace it with the correct IP address including the prefix length (see Fig. 7.16).Press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
Note
The static IP can be disabled by leaving the input box empty.
7.2.2.4.2 Configuring a Network Interface to Use DHCP¶
A network interface can be configured to use DHCP as follows:
- Select the desired interface (see Chapter 7.2.2.4).
- Select DHCP (for IPv4 or IPv6) and press Enter.
7.2.2.4.3 Configuring the Maximum Transmission Unit (MTU)¶
Note
The configuration of the MTU is only possible if a static IP address is configured.
Select the desired interface (see Chapter 7.2.2.4).
Select MTU (for IPv4 or IPv6) and press Enter.
Enter the MTU in the input box.
Press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
Note
If the input box is left empty, the default value is set.
7.2.2.4.4 Using the Router Advertisement for IPv6¶
If the configuration of IP addresses and a global gateway should be performed automatically for IPv6 via SLAAC (Stateless Address Autoconfiguration), router advertisement can be enabled as follows:
- Select the desired interface (see Chapter 7.2.2.4).
- Select Router-advertisement and press Enter.
7.2.2.4.5 Configuring VLANs¶
Note
VLAN interfaces are currently not supported on virtual appliances. If the hypervisor supports virtual switches, this can be used to realize the functionality.
A new VLAN subinterface can be created as follows:
Select the desired interface (see Chapter 7.2.2.4).
Select Configure the VLAN interfaces on this interface and press Enter.
Select Configure a new VLAN interface and press Enter.
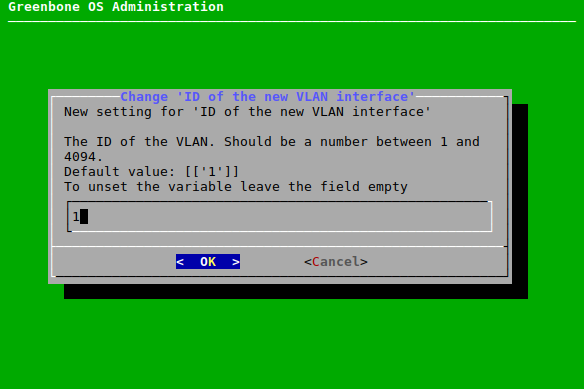
Enter the VLAN ID in the input box and press Enter (see Fig. 7.17).
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
→ The new interface can be configured using IPv4 and IPv6 (see Fig. 7.18).
All created subinterfaces can be configured as follows:
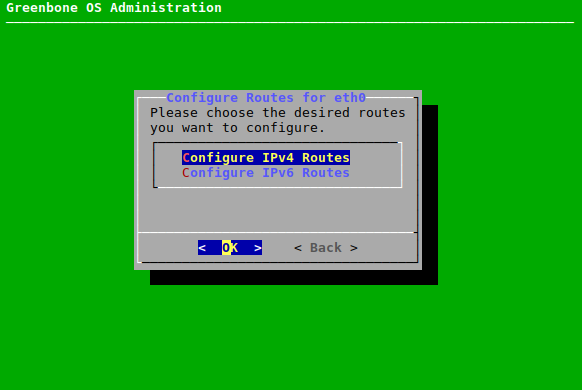
7.2.2.4.6 Configuring the Routes for an Interface¶
A new route for an interface can be configured as follows:
Select the desired interface (see Chapter 7.2.2.4).
Select Configure the Routes for this interface and press Enter.
Select Configure IPv4 Routes or Configure IPv6 Routes and press Enter (see Fig. 7.19).
Select Add a new route and press Enter.
Enter the target network and the next hop in the input boxes, select OK and press Enter.
All created routes can be configured as follows:
- Select the desired interface (see Chapter 7.2.2.4).
- Select Configure the Routes for this interface and press Enter.
- Select Configure IPv4 Routes or Configure IPv6 Routes and press Enter.
- Select the desired route and press Enter.
- Edit the route, select OK and press Enter.
7.2.2.5 Configuring the DNS Server¶
For receiving the feed and updates, the appliance requires a reachable and functioning DNS (Domain Name System) server for name resolution. This setting is not required if the appliance uses a proxy for downloading the feed and updates.
If DHCP is used for the configuration of the network interfaces, the DNS servers provided by the DHCP protocol are used.
The appliance supports up to three DNS servers. At least one DNS server is required. Additional servers will only be used if an outage of the first server occurs.
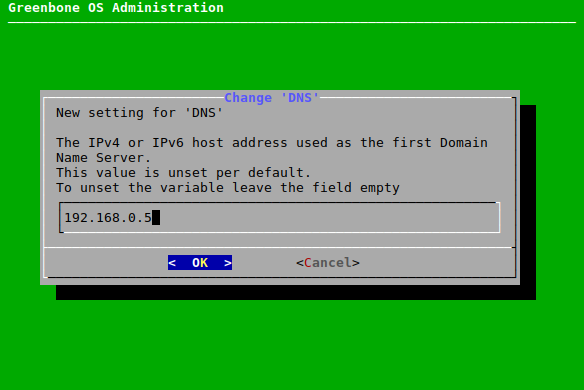
The DNS server can be configured as follows:
Select Setup and press Enter.
Select Network and press Enter.
Select Namespace: Management and press Enter.
Select DNS and press Enter.
Select the desired DNS server and press Enter.
Enter the IP address used as the DNS server in the input box and press Enter (see Fig. 7.20).
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
Note
Whether the DNS server can be reached and is functional can be determined by performing a self-check (see Chapter 7.3.1).
7.2.2.6 Configuring the Global Gateway¶
The global gateway may be obtained automatically using DHCP or router advertisements. The global gateway is often called the default gateway as well.
Note
If the appliance is configured to use static IP addresses exclusively and access to other networks is desired, the global gateway has to be configured manually. Separate options are available for IPv4 and IPv6.
If using DHCP to assign IP addresses, the global gateway will be set via DHCP unless the global gateway has been set explicitly.
If SLAAC (Stateless Address Autoconfiguration) should be used with IPv6, the router advertisement must be activated (see Chapter 7.2.2.4.4).
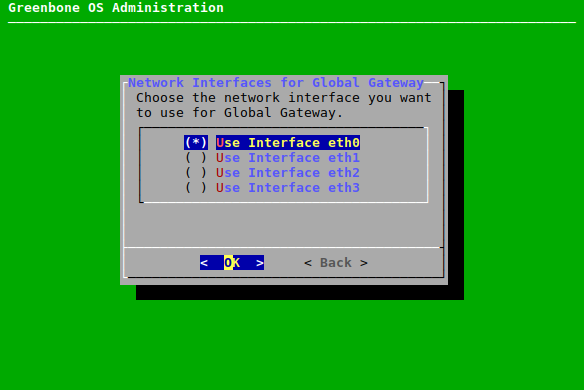
The global gateway can be configured as follows:
Select Setup and press Enter.
Select Network and press Enter.
Note
If the appliance has namespaces (see Chapter 7.2.2.2), the desired namespace has to be selected first.
If the appliance has no namespaces, continue with step 4.
Select the namespace for which the global gateway should be configured and press Enter.
Select Global Gateway for IPv4 or Global Gateway (IPv6) for IPv6 and press Enter.
Select the desired interface and press Enter (see Fig. 7.21).
Enter the IP address used as the global gateway in the input box and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
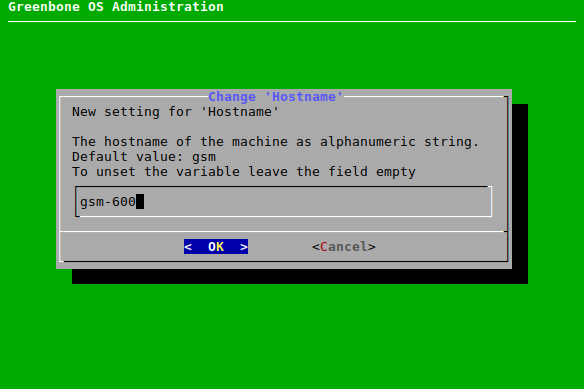
7.2.2.7 Setting the Host Name and the Domain Name¶
While the appliance does not require a special host name, the host name is an important item when creating certificates and sending e-mails.
The host name is used to configure the short host name and the domain name option is used for the domain suffix. The factory default values are:
- Host name: gsm
- Domain name: gbuser.net
The host name and the domain name can be configured as follows:
Select Setup and press Enter.
Select Network and press Enter.
Select Namespace: Management and press Enter.
Select Hostname or Domainname and press Enter.
Enter the host name or the domain name in the input box and press Enter (see Fig. 7.22).
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
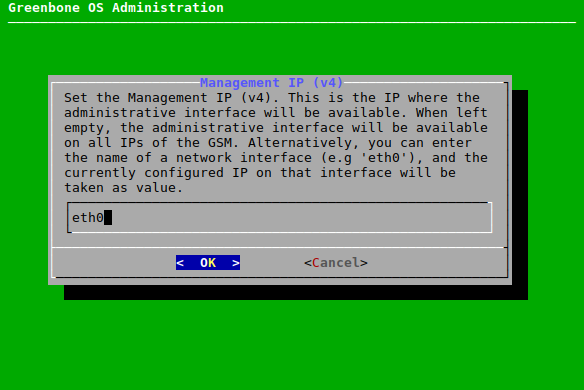
7.2.2.8 Restricting the Management Access¶
The IP address on which the management interface is available can be set.
All administrative access (SSH, HTTPS, GMP) will be restricted to the respective interface and will not be available on the other interfaces.
Note
This feature overlaps with the separation of namespaces (see Chapter 7.2.2). Separating the namespaces is recommended.
Note
If no IP address is set, the management interface will be available on all IP addresses of interfaces in the management namespace.
The IP address for the management interface can be set as follows:
- Select Setup and press Enter.
- Select Network and press Enter.
- Select Namespace: Management and press Enter.
- Select Management IP (v4) or Management IP (v6) and press Enter.
Enter the IP address for the management interface in the input box and press Enter (see Fig. 7.23).
Note
The IP address has to be the IP address of one of the interfaces in the management namespace. If another IP address is set, the management interface will not be available.
Either the IP address or the name of the interface (e.g.,
eth0) can be entered.
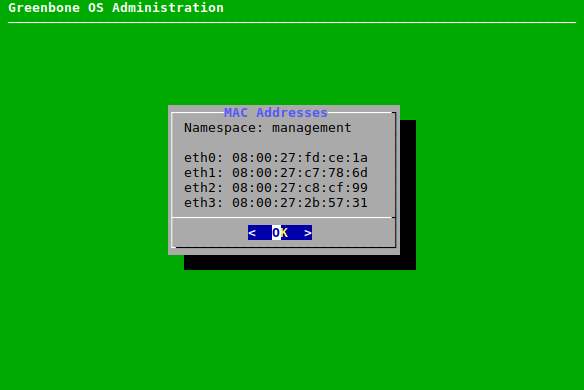
7.2.2.9 Displaying the MAC and IP Addresses and the Network Routes¶
The used MAC addresses, the currently configured IP addresses and the network routes of the appliance can be displayed in a simple overview.
Note
This does not support the configuration of the MAC addresses.
The MAC and IP addresses of the interfaces or network routes can be displayed as follows:
Select Setup and press Enter.
Select Network and press Enter.
Select the namespace for which the IP addresses, MAC addresses or network routes should be displayed and press Enter.
Select MAC, IP or Routes and press Enter.
→ The MAC/IP addresses or the network routes of the selected namespace are displayed (see Fig. 7.24).
7.2.3 Configuring a Virtual Private Network (VPN) Connection¶
OpenVPN is integrated in GOS. To run scans through a VPN tunnel, a VPN connection has to be set up.
Note
Scanning through a VPN tunnel is only available for the appliance models Greenbone Enterprise DECA/TERA/PETA/EXA.
The VPN feature allows for targets that are reachable via the VPN tunnel to be scanned, but has no effect on other targets, network settings, or master-sensor connections.
The VPN tunnel is always initiated from the appliance side.
For the authentication of the appliance in the VPN, a PKCS#12 file with the following requirements is needed:
- The PKCS#12 file must contain the necessary certificate, and private key files.
- The PKCS#12 file may contain a certificate authority (CA) file. If it does not contain one, the CA file must be imported separately.
- The PKCS#12 file may be password protected or not.
- Password protected private key files within the PKCS#12 file are not supported.
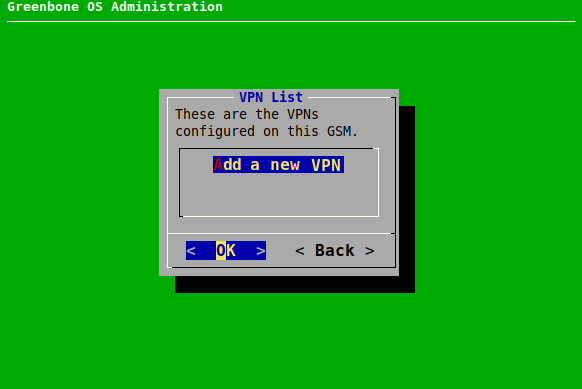
7.2.3.1 Setting up a VPN Connection¶
Note
Only one VPN connection can be set up at a time.
A new VPN connection can be set up as follows:
Select Setup and press Enter.
Select VPN and press Enter.
Select Add a new VPN and press Enter (see Fig. 7.25).
Enter the IP address of the VPN in the input box and press Enter.
Open the web browser and enter the displayed URL.
Click Browse…, select the PKCS#12 container and click Upload.
If an export password was used to protect the PKCS#12 container, enter the password and press Enter.
→ A message informs that the PKCS#12 file was successfully extracted.
Press Enter.
Note
If the PKCS#12 file does not contain a CA file, the CA file must be imported separately.
If the PKCS#12 file already contains a CA file, a CA file can also be imported separately, but this overwrites the CA file from the PKCS#12 file.
Select Certificate Authority and press Enter.
Open the web browser and enter the displayed URL.
Click Browse…, select the CA file and click Upload.
→ A message informs that the CA file was imported successfully.
Press Enter.
→ The VPN connection is established and targets reachable via the VPN can be scanned (see Chapter 10.2).
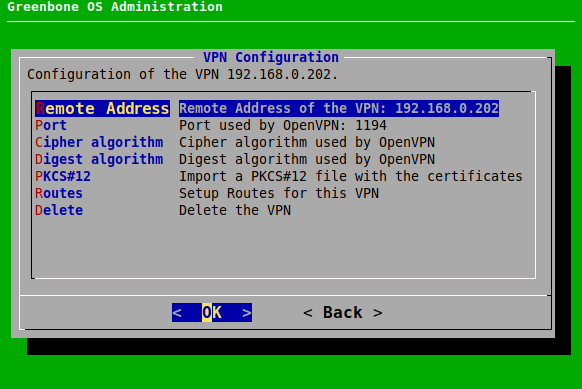
7.2.3.2 Editing or Deleting a VPN Connection¶
The VPN connection can be edited as follows:
Select Setup and press Enter.
Select VPN and press Enter.
The following actions are available:
- Remote Address
- Define the IP address of the VPN.
- Port
- Define the port used by OpenVPN. By default, the port is 1194.
- Cipher algorithm
- Select the cipher algorithm. By default, the default setting of OpenVPN is used.
- Digest algorithm
- Select the digest algorithm. By default, the default setting of OpenVPN is used.
- PKCS#12
- Replace the PKCS#12 file.
- Routes
Add a route for the VPN connection. Target IP address, net mask and target gateway have to be defined.
Note
Only one route can be set up for the VPN connection.
- Delete
- Delete the VPN connection.
7.2.4 Configuring Services¶
To access the appliance remotely, many interfaces are available:
- HTTPS, see Chapter 7.2.4.1
- Greenbone Management Protocol (GMP), see Chapter 15
- Open Scanner Protocol (OSP), see Chapter 7.2.4.3
- SSH, see Chapter 7.2.4.4
- SNMP, see Chapter 7.2.4.5
7.2.4.1 Configuring HTTPS¶
The web interface is the usual option for the creation, execution and analysis of vulnerability scans. It is activated by default and cannot be deactivated.
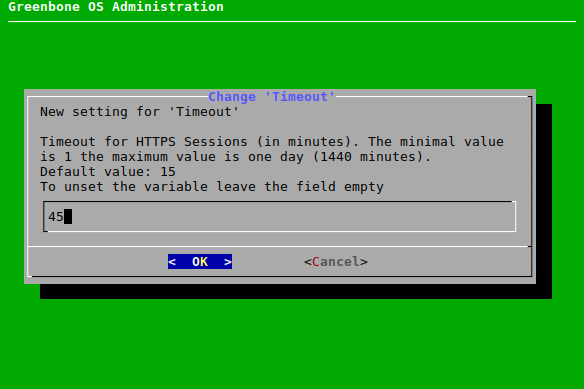
7.2.4.1.1 Configuring the Timeout of the Web Interface¶
The timeout value of the web interface can be set as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
Select Timeout and press Enter.
Enter the desired value for the timeout in the input box and press Enter.
Note
The value can be between 1 and 1440 minutes (1 day). The default is 15 minutes.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
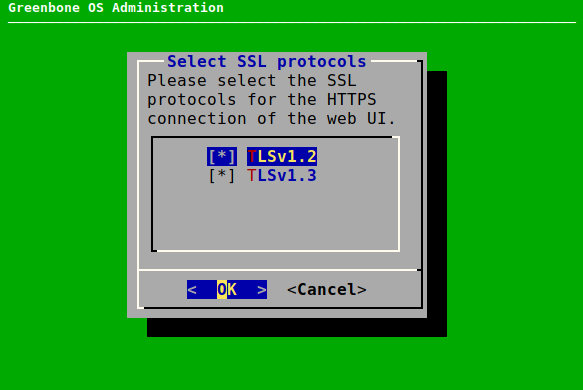
7.2.4.1.2 Configuring the Protocols¶
The protocols for the HTTPS connection of the web interface can be configured as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
Select Protocols and press Enter.
Select the desired protocol version and press Space (see Fig. 7.28).
Note
By default, both versions are selected.
If TLSv1.2 is selected (either alone or in combination with version 1.3), the ciphers for the HTTPS connection can be configured (see Chapter 7.2.4.1.3).
If only TLSv1.3 is selected, the default value for
-ciphersuites valof OpenSSL for the cipher suites is used. In this case, the menu option for configuring the ciphers (see Chapter 7.2.4.1.3) is not available.Select OK and press Enter.
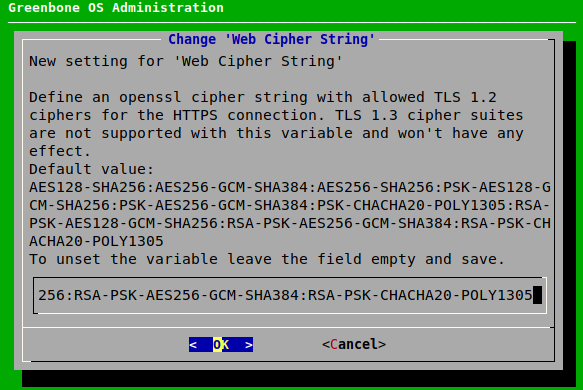
7.2.4.1.3 Configuring the Ciphers¶
If TLS version 1.2 is used for the HTTPS connection of the web interface (either alone or in combination with version 1.3, see Chapter 7.2.4.1.2), the HTTPS ciphers can be configured. The current setting allows only secure ciphers using at least 128 bit key length, explicitly disallowing the cipher suites used by SSLv3 and TLSv1.0. Note that for TLSv1.1 no ciphers exist.
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
Select Ciphers and press Enter.
Enter the desired value in the input box and press Enter (see Fig. 7.29).
Note
The string used to define the ciphers is validated by OpenSSL and must comply with the syntax of an OpenSSL cipher list.
More information about the syntax can be found here.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
7.2.4.1.4 Configuring the Diffie-Hellman (DH) Parameters¶
DH parameters are used by the web server for establishing SSL connections. New DH parameters can be generated as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
Select DH Parameters and press Enter.
Select the desired key size and press Space.
Press Enter.
→ A message informs that the generation was started in the background.
Tip
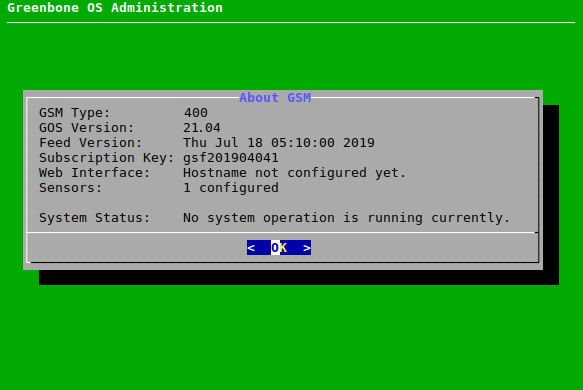
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
7.2.4.1.5 Configuring HTTP STS¶
If web browsers should only access the web interface using HTTPS – instead of HTTP – HTTP Strict Transport Security (HSTS) can be enabled. In addition to enabling HSTS, an HTTPS certificate signed by a certificate authority (CA) is required for HSTS to work (see Chapter 7.2.4.1.7.2).
HSTS can be enabled as follows:
- Select Setup and press Enter.
- Select Services and press Enter.
- Select HTTPS and press Enter.
- Select HTTP STS and press Enter to enable or disable HTTP STS.
If HTTP STS is enabled, the maximum allowed age for the HTTP STS header can be set as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
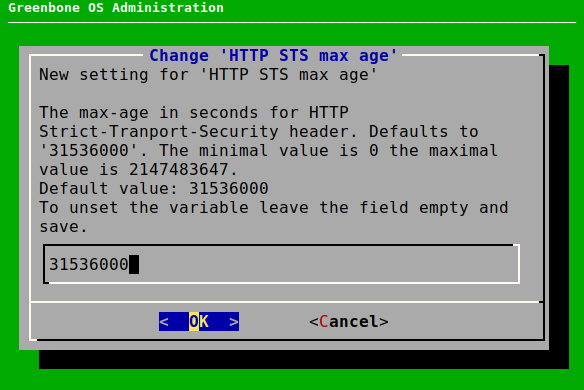
Select HTTP STS max age and press Enter.
Enter the maximal age in seconds in the input box and press Enter (see Fig. 7.30).
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
7.2.4.1.6 Configuring OCSP Stapling¶
OCSP (Online Certificate Status Protocol) stapling is used for checking the validity status of X.509 digital certificates. It allows the certified party to perform the certificate validation by appending a time-stamped OCSP response signed by the certificate authority (CA) to the original TLS handshake (“stapling”).
OCSP stapling can be enabled as follows:
- Select Setup and press Enter.
- Select Services and press Enter.
- Select HTTPS and press Enter.
- Select OCSP Stapling and press Enter to enable or disable OCSP Stapling.
7.2.4.1.7 Managing Certificates¶
The appliance basically uses two types of certificates:
- Self-signed certificates
- Certificates issued by an external certificate authority (CA)
All modern operating systems support the creation and management of their own CA. Under Microsoft Windows Server the Active Directory Certificate Services support the administrator in the creation of a root CA. For Linux systems various options are available. One option is described in the IPSec-Howto.
When creating and exchanging certificates it needs to be considered that the administrator verifies how the systems are accessed later before creating the certificate. The IP address or the DNS name is stored when creating the certificate.
The current certificate can be displayed as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
Select Certificate and press Enter.
Select Show and press Enter.
→ The certificte is displayed.
7.2.4.1.7.1 Self-Signed Certificates¶
The use of self-signed certificates is the easiest way. It poses, however, the lowest security and more work for the user:
- The trustworthiness of a self-signed certificate can only be checked manually by the user through importing the certificate and examining its fingerprint.
- Self-signed certificates cannot be revoked. Once they are accepted by the user, they are stored permanently in the browser. If an attacker gains access to the corresponding private key a man-in-the-middle attack on the connection protected by the certificate can be launched.
To support a quick setup, the appliance supports self-signed certificates. For most appliance models, such a certificate is not installed by default and must be created by the administrator. The Greenbone Enterprise ONE, however, already comes with a pre-installed certificate.
Self-signed certificates can be easily created as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
Select Certificate and press Enter.
Select Generate and press Enter.
→ A message informs that the current certificate and private key will be overwritten.
Confirm the message by selecting Yes and pressing Enter.
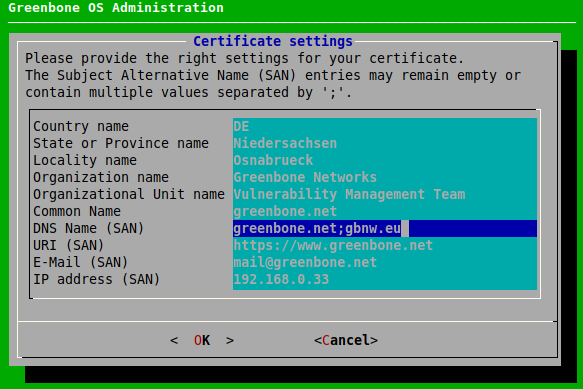
Provide the settings for the certificate (see Fig. 7.31), select OK and press Enter.
Note
It is valid to generate a certificate without a common name. However, a certificate should not be created without (a) Subject Alternative Name(s).
If a common name is used, it should be the same as one of the SANs.
→ When the process is finished, a message informs that the certificate can be downloaded.
Press Enter to close the message.
Select Download and press Enter.
Open the web browser and enter the displayed URL.
Download the PEM file.
In the GOS administration menu, press Enter.
→ When the certificate is retrieved by the appliance, the GOS administration menu displays the fingerprint of the certificate for verification.
Check the fingerprint and confirm the certificate by pressing Enter.
7.2.4.1.7.2 Certificate by an External Certificate Authority (CA)¶
The use of a certificate issued by a CA has several advantages:
- All clients trusting the authority can verify the certificate directly and establish a security connection. No warning is displayed in the browser.
- The certificate can be revoked easily by the CA. If the clients have the ability to check the certificate status they can decline a certificate that may still be within its validity period but has been revoked. As mechanisms the Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) can be used.
- Especially if multiple systems within an organization serve SSL/TLS protected information, the use of an organizational CA simplifies the management drastically. All clients simply have to trust the organizational CA to accept all the certificates issued by the CA.
To import a certificate by an external CA two options are available:
- Generate a certificate signing request (CSR) on the appliance, sign it using an external CA and import the certificate.
- Generate a CSR and the certificate externally and import both using a PKCS#12 file.
Note
The appliance’s web interface cannot be used while waiting for CA to process the CSR. Only after the signed certificate has been imported, the web interface is accessible again.
A new CSR can be created and the certificate can be imported as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
Select Certificate and press Enter.
Select CSR and press Enter.
→ A message informs that the current certificate and private key will be overwritten.
Confirm the message by selecting Yes and pressing Enter.
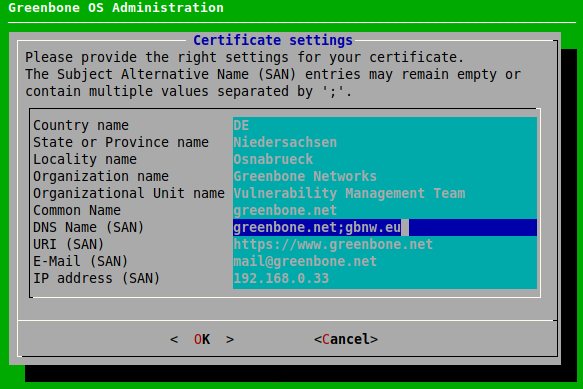
Provide the settings for the certificate (see Fig. 7.32), select OK and press Enter.
Note
It is valid to generate a certificate without a common name. A certificate should not be created without (a) Subject Alternative Name(s).
If a common name is used, it should be the same as one of the SANs.
Open the web browser and enter the displayed URL.
Download the PEM file.
→ The GOS administration menu displays a message to verify that the CSR has not been tampered with.
Verify the information by pressing Enter.
When the certificate is signed, select Certificate and press Enter.
Open the web browser and enter the displayed URL.
Click Browse…, select the signed certificate and click Upload.
→ When the certificate is retrieved by the appliance, the GOS administration menu displays the fingerprint of the certificate for verification.
Check the fingerprint and confirm the certificate by pressing Enter.
If a private key and a signed certificate which should be used for the appliance are already available, they can be imported. The private key and the certificate need to be formatted as a PKCS#12 file. The file can be protected using an export password.
The PKCS#12 file can be imported as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
Select Certificate and press Enter.
Select PKCS#12 and press Enter.
→ A message informs that the current certificate and private key will be overwritten.
Confirm the message by selecting Yes and pressing Enter.
Open the web browser and enter the displayed URL.
Click Browse…, select the PKCS#12 container and click Upload.
Note
If an export password was used to protect the PKCS#12 container, the password has to be entered.
→ When the certificate is retrieved by the appliance, the GOS administration menu displays the fingerprint of the certificate for verification.
Check the fingerprint and confirm the certificate by pressing Enter.
7.2.4.1.8 Displaying Fingerprints¶
The fingerprints of the used certificate can be checked and displayed as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select HTTPS and press Enter.
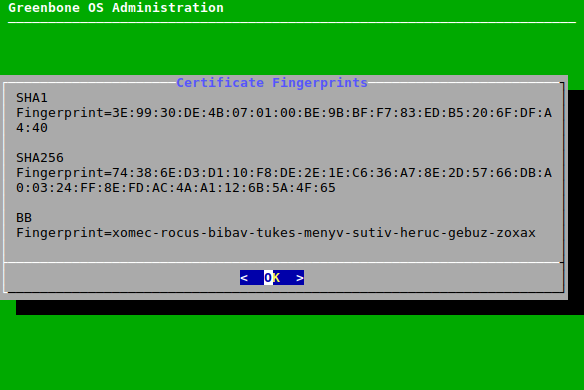
Select Fingerprints and press Enter.
→ The following fingerprints of the currently active certificate are displayed:
- SHA1
- SHA256
- BB
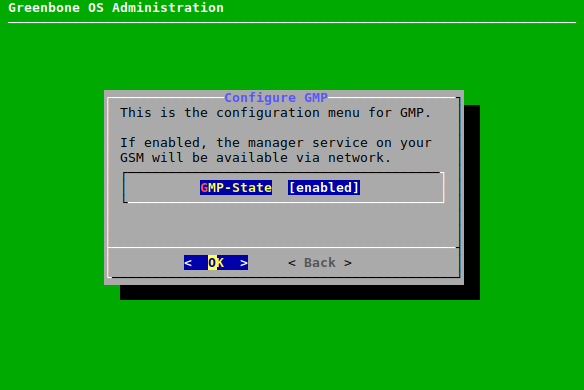
7.2.4.2 Configuring the Greenbone Management Protocol (GMP)¶
The Greenbone Management Protocol (GMP) allows for the communication with other Greenbone products (e.g., an additional appliance). It is required for the master-sensor communication (see Chapter 16).
Additionally, it can be used for the communication of in-house software with the appliance.
GMP can be activated using the GOS administration menu as follows:
Note
The SSH service has to be enabled before GMP can be enabled (see Chapter 7.2.4.4).
7.2.4.3 Configuring the Open Scanner Protocol (OSP)¶
The Open Scanner Protocol (OSP) can be activated using the GOS administration menu as follows:
Note
The SSH service has to be enabled before OSP can be enabled (see Chapter 7.2.4.4).
Select Setup and press Enter.
Select Services and press Enter.
Select OSP and press Enter.
Press Enter to enable or disable OSP.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
7.2.4.4 Configuring SSH¶
SSH allows secure and remote access to the appliance’s GOS administration menu and command line over an unsecured network. Additionally, SSH is required for the master-sensor communication (see Chapter 16).
By default, SSH is disabled on an appliance and must be activated first, e.g., by using the serial console.
An SSH client is also required to connect to the appliance. When connecting to the appliance with an SSH client, the following key exchange methods are supported: ecdh-sha2-nistp256, ecdh-sha2-nistp384, ecdh-sha2-nistp521, curve25519-sha256, curve25519-sha256@libssh.org.
Note
When connecting from an appliance to another system, the supported methods depend both on the other system and the appliance. There are many possible combinations, which are not documented here due to the scope.
7.2.4.4.1 Enabling the SSH State¶
The SSH server embedded in the appliance can be enabled in the GOS administration menu as follows:
- Select Setup and press Enter.
- Select Services and press Enter.
- Select SSH and press Enter.
- Select SSH State and press Enter to enable SSH.
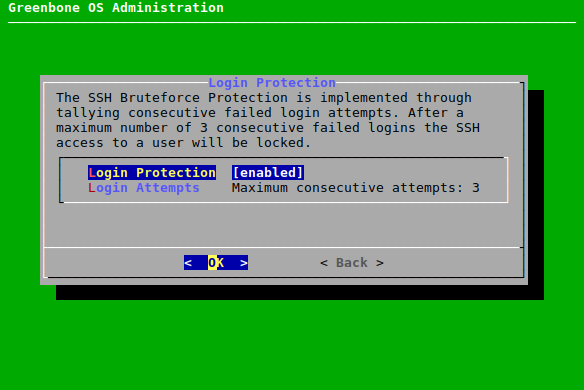
7.2.4.4.2 Enabling and Managing a Login Protection¶
A login protection can be enabled. If a number of consecutive login attempts fail, the user will be locked.
Note
A self-scan, i.e., a scan where the appliance is part of the scan target, may trigger the login protection.
Note
The login protection does not block logging in via SSH admin key if such a key is set up (see Chapter 7.2.4.4.3).
The login protection can be enabled and managed as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select SSH and press Enter.
Select Login Protection and press Enter.
Select Login Protection and press Enter (see Fig. 7.35).
→ A message informs that the login protection can lead to a locked SSH access.
Select Continue and press Enter to enable the login protection.
Select Login Attempts and press Enter.
Enter the desired value and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
In case the system is locked after too many failed login attempts, it has to be unlocked using console access (serial, hypervisor or monitor/keyboard) as follows:
Select Setup and press Enter.
Select User and press Enter.
Select Unlock SSH and press Enter.
→ The login attempt counter is reset.
Press Enter to close the message.
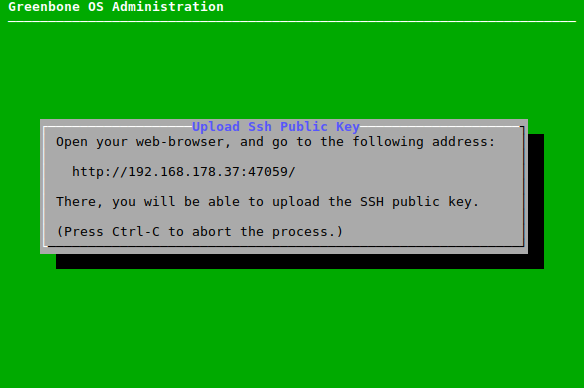
7.2.4.4.3 Adding an SSH Admin Key¶
SSH public keys can be uploaded to enable key-based authentication of administrators.
Note
SSH keys can be generated with OpenSSH by using the command ssh-keygen on Linux or puttygen.exe if using PuTTY on Microsoft Windows.
The formats Ed25519 or RSA are supported.
All SSH keys must correspond to RFC 4716.
An SSH admin key can be uploaded as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select SSH and press Enter.
Select Admin Key and press Enter.
Open the web browser and enter the displayed URL (see Fig. 7.36).
Click Browse…, select the SSH public key and click Upload.
→ When the upload is completed, a message informs that the login via SSH is possible.
7.2.4.4.4 Displaying Fingerprints¶
The appliance provides different host keys for its own authentication. The client decides which public key to use. In the GOS administration menu the fingerprint of the public keys used by the SSH server of the appliance can be displayed as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select SSH and press Enter.
Select Fingerprint and press Enter.
→ The SHA256 fingerprints of the following keys are displayed:
- ED25519
- RSA
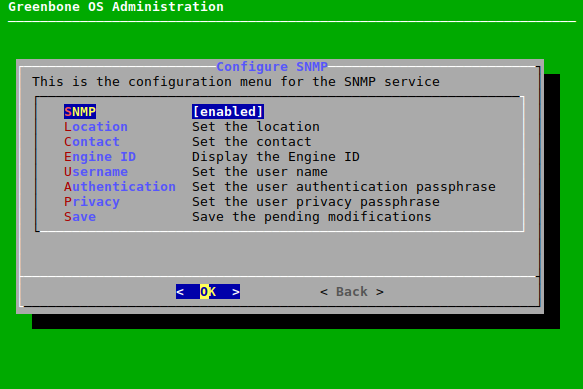
7.2.4.5 Configuring SNMP¶
SNMP read access of the appliance is possible via SNMPv3. The SNMP support can be used for sending traps through alerts and monitoring of vital parameters of the appliance.
The supported parameters are specified in a Management Information Base (MIB) file. The current MIB is available from the Greenbone Tech-Doc-Portal.
The appliance supports SNMPv3 for read access and SNMPv1 for traps.
The SNMPv3 can be configured as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select SNMP and press Enter.
Select SNMP and press Enter to enable SNMP.
→ Several new options are displayed (see Fig. 7.37).
Select Location and press Enter.
Enter the location of the SNMP service in the input box and press Enter.
Select Contact and press Enter.
Enter the contact of the SNMP service in the input box and press Enter.
Select Username and press Enter.
Enter the SNMP user name in the input box and press Enter.
Note
When configuring the authentication and privacy passphrase be aware of the fact that the appliance uses SHA-1 and AES128 respectively.
Select Authentication and press Enter.
Enter the SNMP user authentication passphrase in the input box and press Enter.
Select Privacy and press Enter.
Enter the SNMP user privacy passphrase in the input box and press Enter.
Note
After a user has been configured, the engine ID of the appliance can be displayed by selecting Engine ID and pressing Enter.
Afterwards, test read access of the SNMP service under Linux/Unix using
snmpwalk:
$ snmpwalk -v 3 -l authPriv -u user -a sha -A password -x aes -X key 192.168.222.115
iso .3.6.1.2.1.1.1.0 = STRING: "Greenbone Security Manager"
iso .3.6.1.2.1.1.5.0 = STRING: "gsm"
...
The following information can be gathered:
- Uptime
- Network interfaces
- Memory
- Harddisk
- Load
- CPU
7.2.4.6 Configuring a Port for the Temporary HTTP Server¶
By default, the port for HTTP uploads and downloads is randomly selected.
A permanent port can be configured as follows:
Select Setup and press Enter.
Select Services and press Enter.
Select Temporary HTTP and press Enter.
Select Port and press Enter.
Enter the port in the input box and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
7.2.5 Configuring Periodic Backups¶
The appliance supports automatic daily backups. These backups are stored locally or remote using the following scheme:
- Last 7 daily backups
- Last 5 weekly backups
- Last 12 monthly backups
Backups older than one year will be deleted automatically. In factory state backups are disabled.
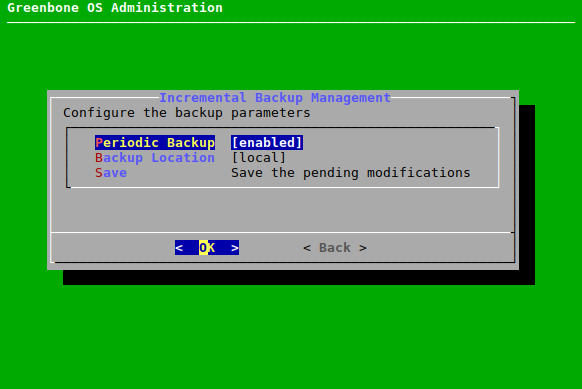
7.2.5.1 Enabling Periodic Backups¶
Periodic backups can be enabled as follows:
Select Setup and press Enter.
Select Backup and press Enter.
Select Periodic Backup and press Enter (see Fig. 7.38).
→ Periodic backups are enabled.
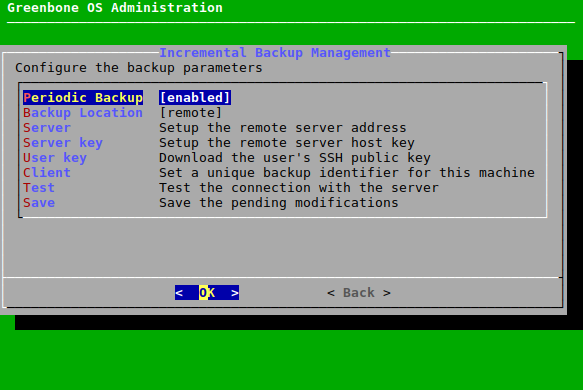
7.2.5.2 Setting up a Remote Backup Server¶
By default, backups are stored locally. To store them on a remote server the server has to be set up appropriately. The appliance uses the Secure File Transfer Protocol (SFTP) supported by SSH to transfer the backups.
Set up a remote server as follows:
Select Setup and press Enter.
Select Backup and press Enter.
Select Backup Location and press Enter.
→ More options for the backup location are added (see Fig. 7.39).
Select Server and press Enter.
Enter the remote server address in the following format:
username@hostname[:port]/directoryNote
The optional port may be omitted if the server uses port 22.
Select OK and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
Note
The appliance uses an SSH host public key to identify the remote server.
The SSH host public key has to be looked up on the remote backup server. On Linux and most Unix-like systems it can be found under
/etc/ssh/ssh_host_*_key.pub.The SSH host public key must be in the OpenSSH Public Key Format. The expected structure is <algorithm> <key> <comment>. The <key> section must be Base64 encoded. The <comment> section is optional. Example: ssh-rsa AAAAB3NzaC1y…P3pCquVb
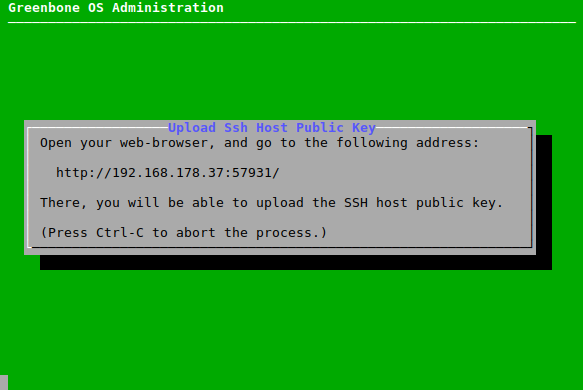
Select Server key and press Enter.
Open the web browser and enter the displayed URL (see Fig. 7.40).
Click Browse…, select the SSH host public key and click Upload.
Note
The appliance uses an SSH public key to log in on the remote server. To enable this login process, the SSH public key of the appliance must be enabled in the
authorized_keysfile on the remote server.To download the public key select User key and press Enter.
Open the web browser and enter the displayed URL.
Download the PUB file.
Note
If several appliances upload their backups to the same remote server, the files must be distinguishable. For this a unique backup identifier has to be defined. If this identifier is not set, the hostname will be used. If the hostname was modified from the default and is unique, the backup files will be distinguishable as well.
Select Client and press Enter.
Enter the identifier and press Enter.
Note
Since the setup of the remote backup including the keys is error-prone, a test routine is available. This option will test the successful login to the remote system.
Select Test and press Enter.
→ The login to the remote system is tested.
7.2.6 Configuring Special Upgrade Settings¶
7.2.6.1 Adding an Upgrade Key¶
Uploading an upgrade key is not required for usual appliance operation and should only be done when instructed by the Greenbone. Greenbone will provide the upgrade key in such a case.
Note
The key is automatically removed when GOS is successfully upgraded.
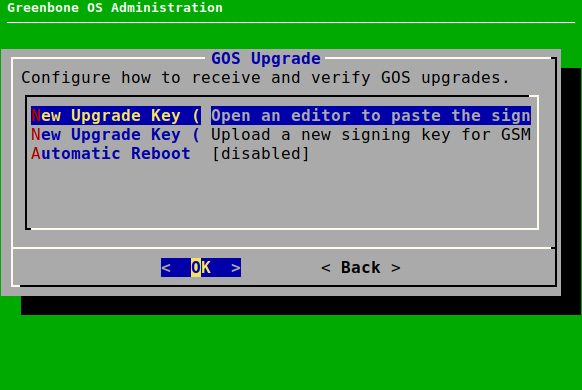
The key can be added using the editor as follows:
Select Setup and press Enter.
Select Upgrade and press Enter.
Select New Upgrade Key (Editor) and press Enter (see Fig. 7.41).
→ The editor is opened.
Enter the content of the upgrade key.
Note
It is important to enter the content of the key and not the name of the key (e.g.,
GBFeedSigningKeyUntil2024.gpg.asc).The content of the key can be displayed with any text editor or under Linux using the program
less. If the content is opened with a text editor, care must be taken to not change anything.Press Ctrl + X.
Press Y to save the changes.
Press Enter.
→ A message informs that the upgrade key was successfully uploaded.
Both menu options for uploading a key are hidden temporarily. Instead, the menu option Delete Upgrade Key is displayed (see Chapter 7.2.6.2).
Press Enter to close the message.
The key can be added using HTTP as follows:
Select Setup and press Enter.
Select Upgrade and press Enter.
Select New Upgrade Key (HTTP) and press Enter (see Fig. 7.41).
Open the web browser and enter the displayed URL.
Click Browse…, select the upgrade key and click Upload.
→ A message informs that the upgrade key was successfully uploaded.
Both menu options for uploading a key are hidden temporarily. Instead, the menu option Delete Upgrade Key is displayed (see Chapter 7.2.6.2).
Press Enter to close the message.
7.2.6.2 Deleting an Upgrade Key¶
An upgrade key can be deleted as follows:
Select Setup and press Enter.
Select Upgrade and press Enter.
Select Delete Upgrade Key and press Enter.
→ A message informs that the upgrade key was deleted.
Press Enter to close the message.
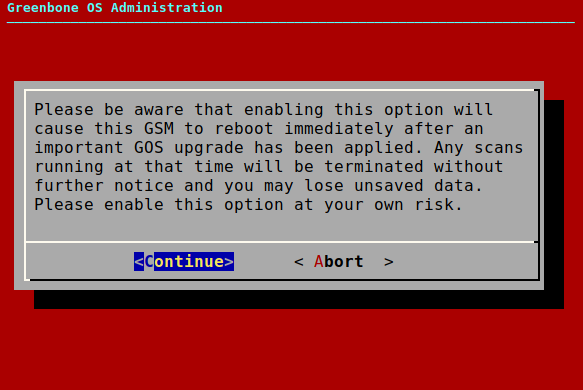
7.2.6.3 Configuring the Automatic Reboot¶
The appliance may reboot automatically after a successful GOS upgrade. However, a reboot is only performed if it is required, e.g., if the Linux kernel of GOS is updated.
The automatic reboot is disabled by default. In this case, a selfcheck warning is displayed after a GOS upgrade that requires a reboot, asking the user to reboot manually.
Note
This setting applies only to the appliance on which it is configured. It does not apply to all sensors connected to the appliance. If sensors should reboot automatically, each sensor must be configured separately.
Select Setup and press Enter.
Select Upgrade and press Enter.
Select Automatic Reboot and press Enter.
→ A warning informs that the appliance will reboot immediately after a GOS upgrade (see Fig. 7.42).
Note
All scans running at that time will be terminated. This can lead to the loss of unsaved data.
Select Continue and press Enter.
Select Save and press Enter.
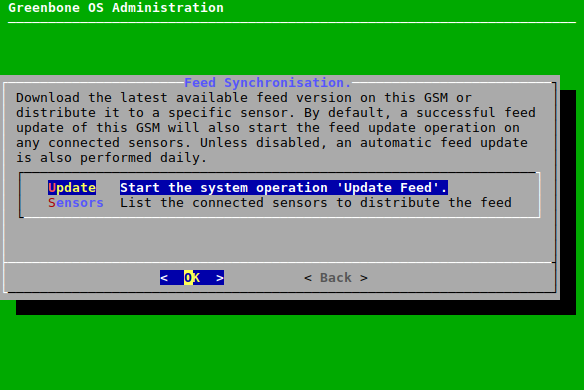
7.2.7 Configuring the Feed Synchronization¶
The Greenbone Enterprise Feed provides updates to the Vulnerability Tests (VT), the SCAP data (CVE and CPE) and the advisories from the CERT-Bund and DFN-CERT. Additionally, the feed provides upgrades for GOS.
A subscription key is required to use the Greenbone Enterprise Feed (see Chapter 7.1.1). This key allows the appliance to download the Greenbone Enterprise Feed provided by Greenbone.
If no valid subscription key is stored on the appliance, the appliance only uses the public Greenbone Community Feed and not the Greenbone Enterprise Feed.
7.2.7.1 Adding a Greenbone Enterprise Feed Subscription Key¶
Note
It is not necessary to add a Greenbone Enterprise Feed subscription key on a newly delivered appliance since a key is already pre-installed.
Whether a subscription key is already present on the appliance can be displayed by selecting About and pressing Enter in the GOS administration menu.
A new subscription key can be stored on the appliance by either uploading it using HTTP or by copying and pasting it using an editor.
For information about the subscription key see Chapter 7.1.1.
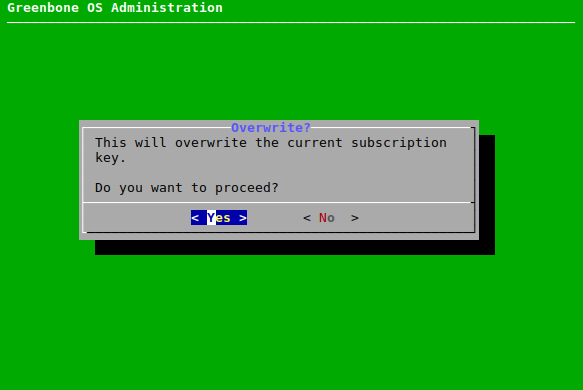
Note
The new key will overwrite any key already stored on the appliance.
When the subscription key is overwritten, the state of the feed on the appliance is reset to “No feed present”. A feed update must be performed after adding the new subscription key.
The key can be added using HTTP as follows:
Select Setup and press Enter.
Select Feed and press Enter.
Select Key(HTTP) and press Enter.
→ A message informs that the current subscription key will be overwritten (see Fig. 7.43).
Select Yes and press Enter.
Open the web browser and enter the displayed URL.
Click Browse…, select the subscription key and click Upload.
→ A message informs that the subscription key was successfully uploaded.
Press Enter to close the message.
The key can be added using the editor as follows:
Select Setup and press Enter.
Select Feed and press Enter.
Select Key(Editor) and press Enter.
→ A message informs that the current subscription key will be overwritten (see Fig. 7.43).
Select Yes and press Enter.
→ The editor is opened.
Enter the content of the subscription key.
Note
It is important to enter the content of the key and not the name of the key (e.g.,
gsf2022122017).The content of the key can be displayed with any text editor or under Linux using the program
less. If the content is opened with a text editor, care must be taken to not change anything.Press Ctrl + X.
Press Y to save the changes.
Press Enter.
→ A message informs that the subscription key was successfully uploaded.
Press Enter to close the message.
7.2.7.2 Enabling or Disabling Synchronization¶
The automatic synchronization of the Greenbone Enterprise Feed can be disabled if the appliance does not have any internet access and should not try to access the Greenbone services on the internet. The synchronization can be enabled again.
The synchronization can be enabled or disabled as follows:
Select Setup and press Enter.
Select Feed and press Enter.
Select Synchronisation and press Enter.
→ The synchronization is enabled.
The synchronization can be disabled by selecting Synchronisation and pressing Enter again.
Note
The time of the automatic feed synchronization can be set by changing the maintenance time (see Chapter 7.2.13).
7.2.7.3 Configuring the Synchronization Port¶
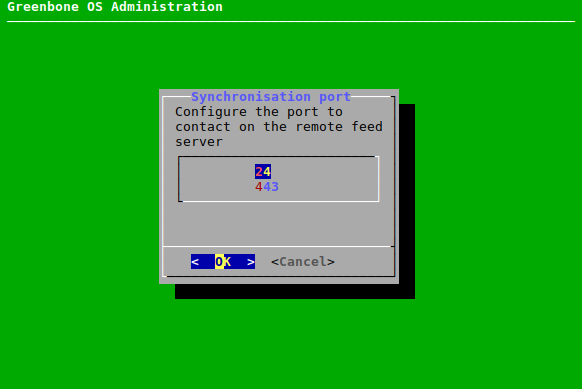
The Greenbone Enterprise Feed is provided by Greenbone on two different ports:
- 24/tcp
- 443/tcp
While port 24/tcp is the default port, many firewall setups do not allow traffic to pass to this port on the internet. So the modification of the port to 443/tcp is possible. This port is most often allowed.
The port can be configured as follows:
Select Setup and press Enter.
Select Feed and press Enter.
Select Greenbone Server and press Enter.
Select Sync port and press Enter.
Select the desired port and press Enter (see Fig. 7.44).
Note
The port 443/tcp is usually used by HTTPS traffic. While the appliance uses this port, the actual traffic is not HTTPS but SSH. The appliance uses rsync embedded in SSH to retrieve the feed. Firewalls supporting deep inspection and application awareness may still reject the traffic if these features are enabled.
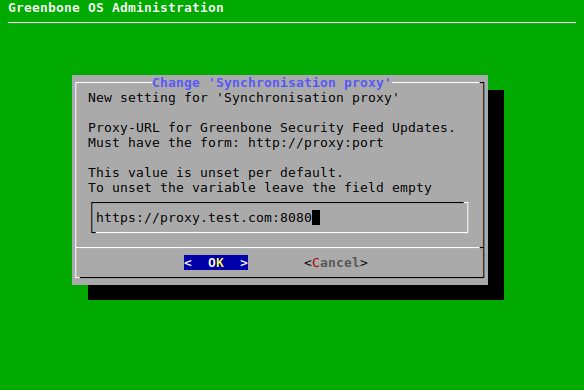
7.2.7.4 Setting the Synchronization Proxy¶
If the security policy does not allow for direct internet access, the appliance can use an HTTPS proxy service. This proxy must not inspect the SSL/TLS traffic but must support the CONNECT method. The traffic passing through the proxy is not HTTPS but SSH encapsulated in http-proxy.
The proxy can be set as follows:
Select Setup and press Enter.
Select Feed and press Enter.
Select Greenbone Server and press Enter.
Select Sync proxy and press Enter.
Enter the URL of the proxy in the input box (see Fig. 7.45).
Note
The URL must have the form
http://proxy:port.
7.2.7.5 Deleting the Greenbone Enterprise Feed Subscription Key¶
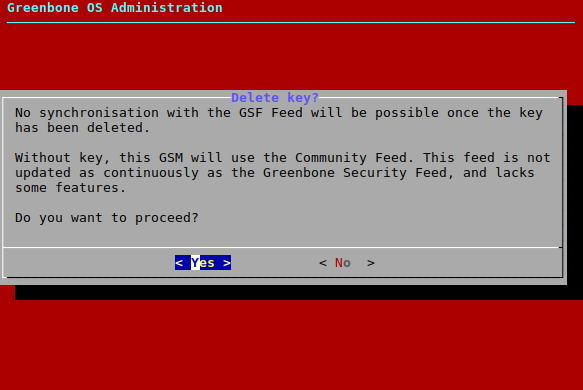
The subscription key can be removed. This is useful if an appliance is at the end of life and is not used anymore. The cleanup ensures that no licenses are left on the appliance. Without the subscription key, the appliance will only retrieve the Greenbone Community Feed.
There is a warning when choosing this option.
The cleanup can be done as follows:
Select Setup and press Enter.
Select Feed and press Enter.
Select Cleanup and press Enter.
→ A warning informs that the synchronization with the Greenbone Enterprise Feed is no longer possible after the cleanup (see Fig. 7.46).
Select Yes and press Enter.
→ A message informs that the subscription key has been deleted.
Press Enter to close the message.
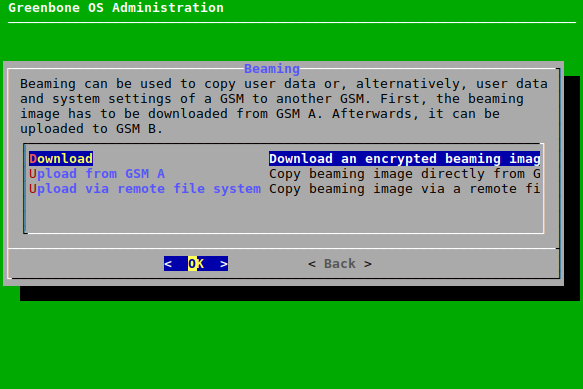
7.2.8 Configuring the Appliance as an Airgap Master/Sensor¶
The Airgap function allows an appliance that is not directly connected to the internet to obtain feed updates and GOS upgrades.
Two appliances are required:
- Airgap sensor: situated in a secured area and is not connected to the internet
- Airgap master: is connected to the internet
Two options are available for the Airgap function:
- Greenbone Airgap USB stick
- Airgap FTP server
The following appliance models can be configured for USB Airgap:
- Greenbone Enterprise 400 and higher as Airgap USB master
- Greenbone Enterprise 400 and higher as Airgap USB sensor
The following appliance models can be configured for FTP Airgap:
- Greenbone Enterprise 400 and higher as Airgap FTP master
- Greenbone Enterprise 150 and higher as Airgap FTP sensor
- Greenbone Enterprise CENO and higher as Airgap FTP sensor
7.2.8.1 Using the Airgap USB Stick¶
The updates and upgrades are loaded from an appliance that is connected to the internet and copied to a USB stick. The USB stick can then can be used to update the second appliance.
Note
The USB stick has to be a specific Airgap USB stick provided by Greenbone. Contact the Greenbone Enterprise Support providing the customer number to request a respective Airgap USB stick.
Tip
The USB stick can be checked for malware by a security gateway beforehand.
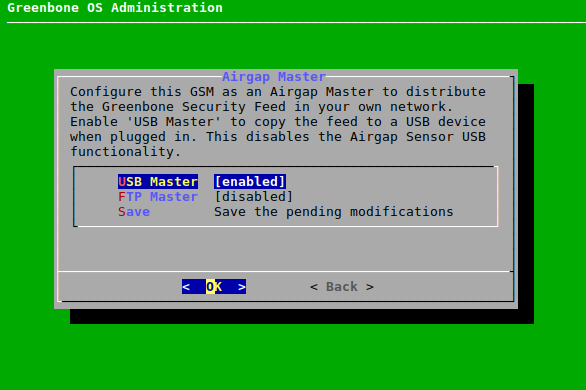
The data transfer using the Airgap USB stick is performed as follows:
In the GOS administration menu of the Airgap master select Setup and press Enter.
Select Feed and press Enter.
Select Airgap Master and press Enter.
Select USB Master and press Enter (see Fig. 7.47).
Select Save and press Enter.
Note
Configuring an appliance as an Airgap USB master disables the possibility to configure the appliance as an Airgap USB sensor.
Connect the Airgap USB stick to the Airgap master.
→ The data transfer starts automatically.
When the data transfer is finished, connect the Airgap USB stick to the Airgap sensor.
→ The data transfer starts automatically.
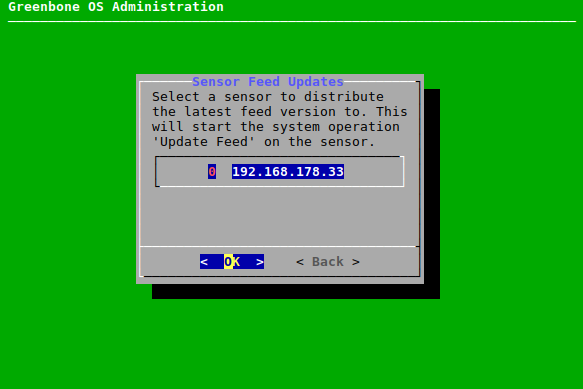
7.2.8.2 Using the Airgap FTP Server¶
The updates and upgrades can be provided via an FTP server operating as a data diode. A data diode is a unidirectional security gateway allowing the data flow in only one direction.
An FTP Airgap update is done when a manual feed update (see Chapter 7.3.6) or an automatic feed update at maintenance time is performed.
Note
Ensure that the Airgap master has enough time to upload the Airgap FTP feed to the FTP server. For slower connections, it may be advisable to set the maintenance time of the Airgap sensor at least three hours behind that of the Airgap master (see Chapter 7.2.9).
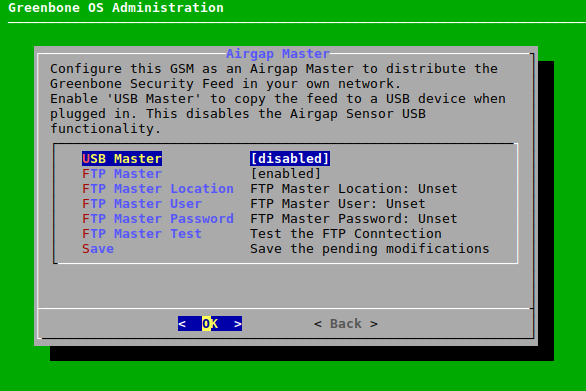
The configuration of an Airgap FTP setup is performed as follows:
In the GOS administration menu of the Airgap master select Setup and press Enter.
Select Feed and press Enter.
Select Airgap Master and press Enter.
Select FTP Master and press Enter.
→ Additional menu options for the configuration of the FTP server are shown (see Fig. 7.48).
Select FTP Master Location and press Enter.
Enter the path of the FTP server in the input box and press Enter.
- The required format for the path is
ftp://1.2.3.4orftp://path.to.ftpserver. - Optionally, a port can be configured, e.g.,
ftp://1.2.3.4:21. - If no port is configured, the default FTP port 21 is used. If a port other than 21 should be used, it must be configured explicitly.
- The required format for the path is
Select FTP Master User and press Enter.
Enter the user used for logging into the FTP server in the input box and press Enter.
Select FTP Master Password and press Enter.
Enter the password used for logging into the FTP server in the input box and press Enter.
Select FTP Master Test and press Enter.
→ It is tested whether a login with the entered information is working.
Select Save and press Enter.
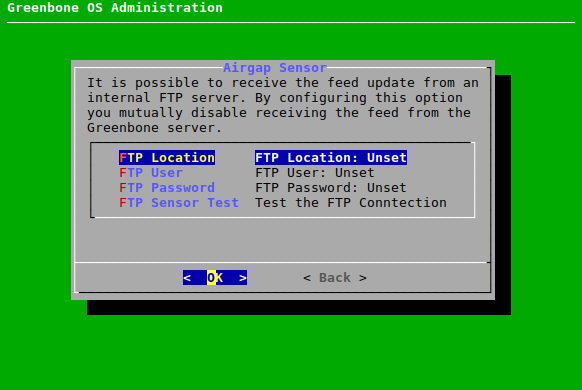
In the GOS administration menu of the Airgap sensor select Setup and press Enter.
Select Feed and press Enter.
Select Airgap Sensor and press Enter.
Execute steps 5 to 12 in the GOS administration menu of the Airgap sensor using the same input as for the Airgap master.
Note
The menu options have slightly different names compared to the GOS administration menu of the Airgap master (see Fig. 7.49).
→ The data transfer starts during the next feed update.
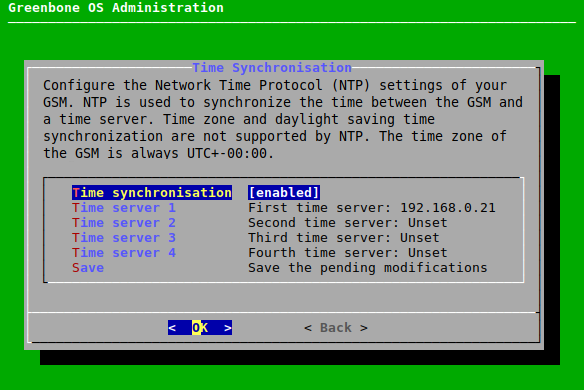
7.2.9 Configuring the Time Synchronization¶
To synchronize the appliance with central time servers, the appliance supports the Network Time Protocol (NTP). Up to four different NTP servers can be configured. The appliance will choose the most suitable server. During an outage of one server, another server will be used automatically.
Both IP addresses and DNS names are supported.
Note
Time zone and daylight saving time synchronization are not supported by NTP. The time zone of the appliance is always UTC±00:00.
The NTP settings can be configured as follows:
Select Setup and press Enter.
Select Timesync and press Enter.
Select Time synchronisation and press Enter.
→ The time synchronization is enabled.
Select the desired time server and press Enter (see Fig. 7.50).
Enter the time server in the input box and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
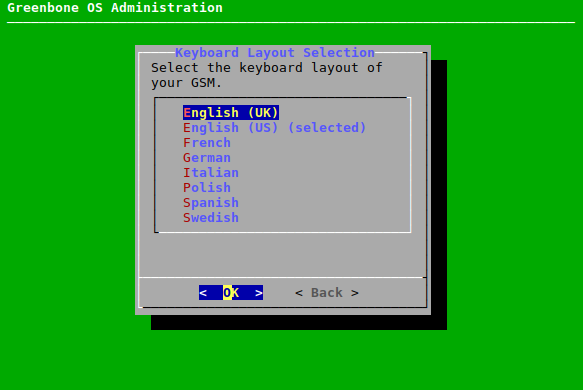
7.2.10 Selecting the Keyboard Layout¶
The keyboard layout of the appliance can be modified as follows:
Select Setup and press Enter.
Select Keyboard and press Enter.
→ All available keyboard layouts are displayed. The current layout has the annotation (selected) (see Fig. 7.51).
Select the desired keyboard layout and press Enter.
→ A message asks to confirm the change.
Select Yes and press Enter.
→ A message informs that the layout has been changed.
7.2.11 Configuring the E-Mails Settings¶
If reports of vulnerability scans or compliance audits should be delivered via e-mail, the appliance must first be connected to a server that acts as a mailhub. Such a server is also called a “mail relay”, “relay host” or “smart host”. By default, the appliance does not deliver e-mails directly to the internet, but only indirectly via the mailhub, through which they must then be forwarded to the recipients’ e-mail servers. The mailhub must support the Simple Mail Transfer Protocol (SMTP).
The appliance does not store e-mails in the event of delivery failure and no second delivery attempt is made.
Note
The appliance implements the Postfix mail transfer agent. The mailhub may need to be set up correctly to work with the appliance. Information about special configurations for this case can be found in the mailhub documentation.
In addition, any mailhub spam protection, such as the gray listing, must be disabled specifically for the appliance.
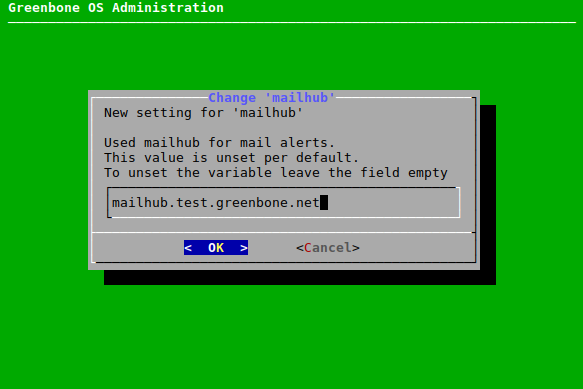
7.2.11.1 Configuring the Mailhub¶
The mailhub can be configured as follows:
Select Setup and press Enter.
Select Mail and press Enter.
Select Mail and press Enter.
Enter the mailhub’s URL in the input box (see Fig. 7.52).
Select OK and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
Note
A port that is used for the mailhub can be configured if desired. However, a manual configuration is not necessary.
If no port is configured, the default ports for SMTP(S) are used automatically.
Select Mailhub Port and press Enter.
Enter the port in the input field and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
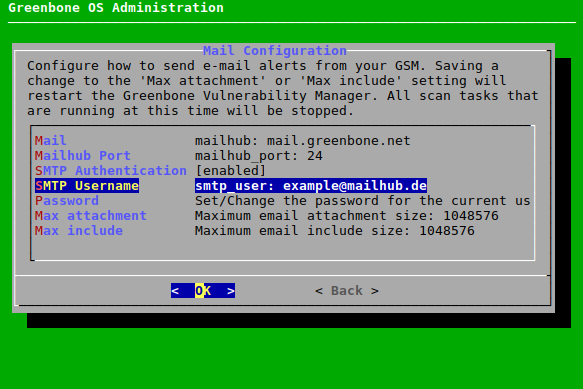
7.2.11.2 Configuring SMTP Authentication for the Mailhub¶
Note
The appliance only supports authentication via the SMTP-Auth extension.
Optionally, SMTP authentication can be configured for the used mailhub as follows:
Select Setup and press Enter.
Select Mail and press Enter.
Select SMTP Authentication Requirements and press Enter to enable SMTP authentication (see Fig. 7.53).
Select SMTP Username and press Enter.
Enter the user name of the account used for authentication in the input field and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
Select Password and press Enter.
Enter the password of the account used for authentication twice and press Tab.
Note
Passwords must not be longer than 128 characters.
Press Enter.
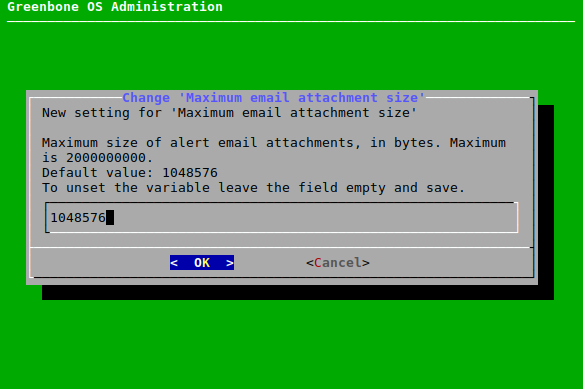
7.2.11.3 Configuring the Size of Included or Attached Reports¶
The maximum size (in bytes) of reports included in or attached to an e-mail (see Chapter 10.12) can be limited as follows:
Select Setup and press Enter.
Select Mail and press Enter.
Select Max attachment or Max include and press Enter.
Enter the maximum size (in bytes) in the input box (see Fig. 7.54).
Select OK and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
7.2.12 Configuring the Collection of Logs¶
The appliance supports the configuration of a central logging server for the collection of logs. Either only the security-relevant logs or all system logs can be sent to a remote logging server.
The security-relevant logs only contain messages from the security and authentication logging facilities:
- auth
- authpriv
- security
Additionally, the full logs contain the following facilities:
- cron
- daemon
- ftp
- kern
- lp
- lpr
- ntp
- news
- syslog
- user
- uucp
- console
- solaris-cron
- local0 – local7
The appliance uses the syslog protocol. Central collection of the logs allows for central analysis, management and monitoring of logs. Additionally, the logs are always stored locally as well.
One logging server can be configured for each kind of log (security-relevant logs or all system logs).
For transfer, UDP (default), TLS, and TCP can be used. TCP ensures the delivery of the logs even if a packet loss occurs. If a packet loss occurs during a transmission via UDP, the logs will be lost. TLS enables an optional authentication of the sender via TLS. This process is not RFC 5425 compliant.
Note
The time zone of the appliance (UTC±00:00) is used for the time stamps of the logs unless adjusted on the syslog server.
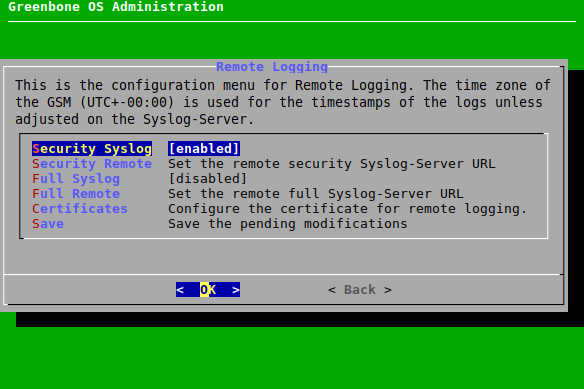
7.2.12.1 Configuring the Logging Server¶
The logging server can be set up as follows:
- Select Setup and press Enter.
- Select Remote Syslog and press Enter.
Select Security Syslog and press Enter to enable security-relevant logs (see Fig. 7.55).
or
Select Full Syslog and press Enter to enable all system logs (see Fig. 7.55).
Note
Both logs can be enabled.
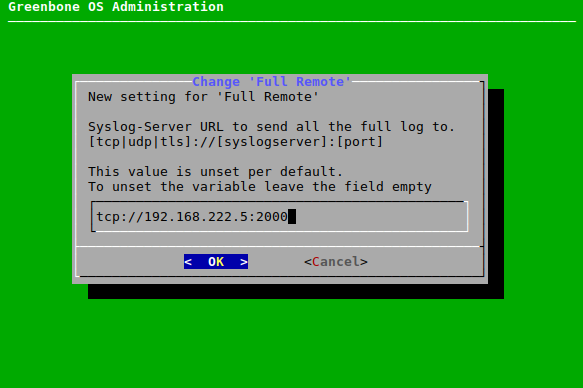
Select Security Remote and press Enter to set the logging server URL for security-relevant logs.
or
Select Full Remote and press Enter to set the logging server URL for all system logs.
Enter the logging server URL in the input box (see Fig. 7.56).
Note
If no port is specified, the default port 514 will be used.
If the protocol is not specified, UDP will be used.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
7.2.12.2 Managing HTTPS Certificates for Logging¶
HTTPS certificates for logging can be managed as follows:
Select Setup and press Enter.
Select Remote Syslog and press Enter.
Select Certificates and press Enter.
Select Generate and press Enter to generate a certificate.
→ A message informs that the current certificate and private key will be overwritten.
Confirm the message by selecting Yes and pressing Enter.
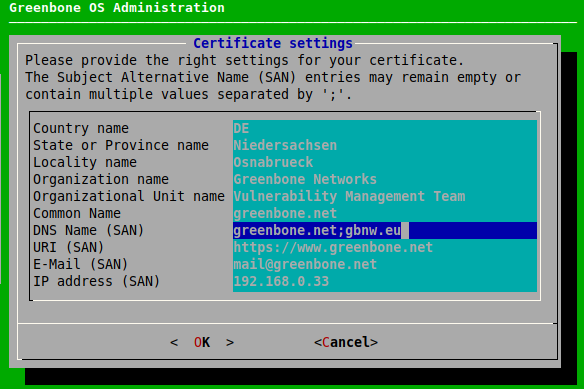
Provide the settings for the certificate (see Fig. 7.57), select OK and press Enter.
Note
It is valid to generate a certificate without a common name. A certificate should not be created without (a) Subject Alternative Name(s).
If a common name is used, it should be the same as one of the SANs.
→ When the process is finished, a message informs that the certificate can be downloaded.
Press Enter to close the message.
Select Certificates and press Enter.
Select Download and press Enter.
Open the web browser and enter the displayed URL.
Download the file.
In the GOS administration menu, press Enter.
→ When the certificate is retrieved by the appliance, the GOS administration menu displays the fingerprint of the certificate for verification.
Check the fingerprint and confirm the certificate by pressing Enter.
The certificate and the according fingerprint can be displayed as follows:
Select Setup and press Enter.
Select Remote Syslog and press Enter.
Select Certificates and press Enter.
Select Show and press Enter to display the certificate.
Select Fingerprints and press Enter to display the fingerprint.
→ The following fingerprints of the currently active certificate are shown:
- SHA1
- SHA256
7.2.13 Setting the Maintenance Time¶
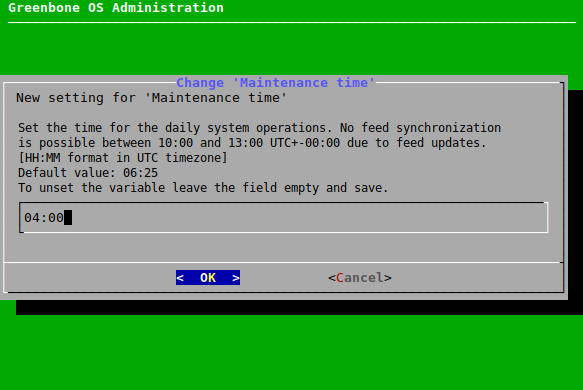
During maintenance, the daily feed synchronization takes place. Any time during the day can be chosen except for 10:00 a.m. to 1:00 p.m. UTC. During this period, Greenbone updates the feed and disables the synchronization services.
The default maintenance time is a random time between 3:00 a.m. and 5:00 a.m. UTC±00:00.
The maintenance time can be set as follows:
Select Setup and press Enter.
Select Time and press Enter.
Enter the desired maintenance time in the input box and press Enter (see Fig. 7.58).
Note
The time has to be converted to UTC before entering it.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
7.3 Maintenance Menu¶
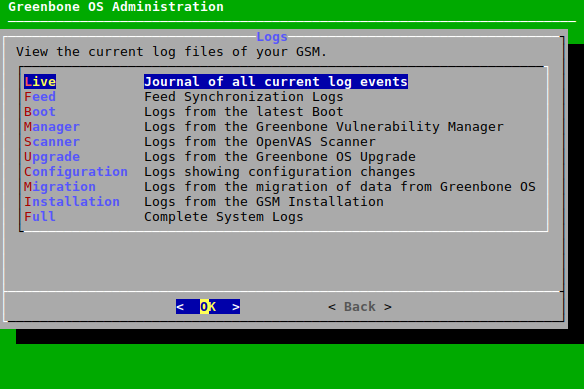
7.3.1 Performing a Self-Check¶
The self-check option checks the setup of the appliance. It displays wrong or missing configuration details which might prevent the correct function of the appliance. The following items are checked:
- Network connection
- DNS resolution
- Feed reachability
- Available updates
- User configuration
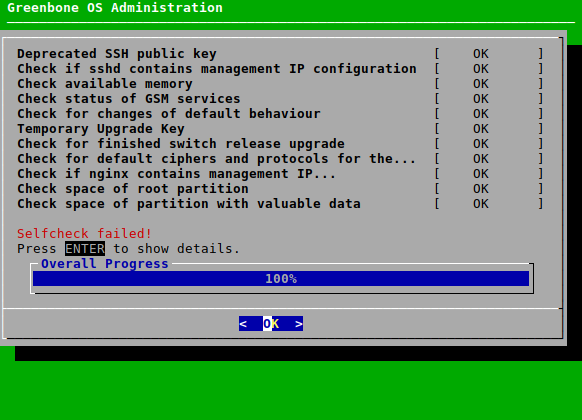
The self-check is performed as follows:
Select Maintenance and press Enter.
Select Selfcheck and press Enter.
→ The self-check is performed. When it is finished, the result is displayed.
Press Enter (see Fig. 7.59).
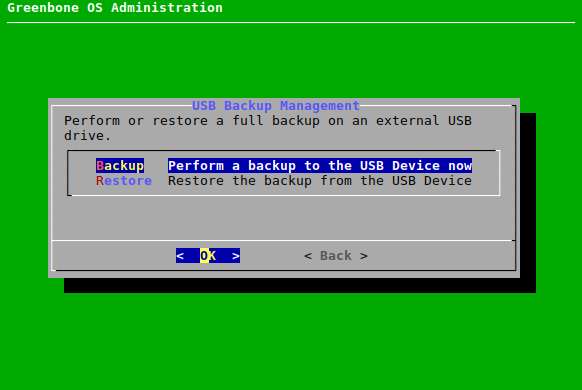
7.3.2 Performing and Restoring a Backup¶
Scheduled local and remote backups are configured in the menu Setup (see Chapter 7.2.5).
Backups can also be performed manually. Depending on the backup location configured within Chapter 7.2.5, the manually triggered backups are stored remotely or locally. These backups can be transferred to a USB stick for offsite storage.
The backup includes user data (e.g., tasks, reports, results) and system settings, i.e., the GOS configuration.
7.3.2.1 Performing a Backup Manually¶
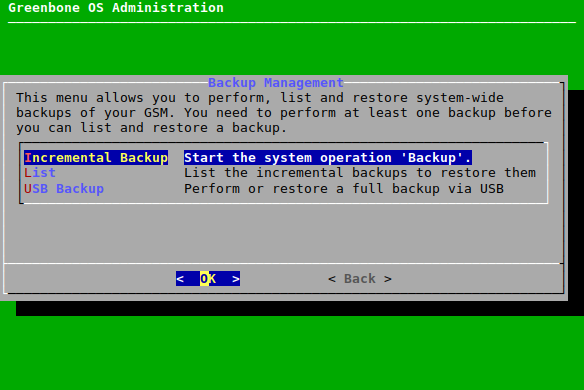
A backup can be performed manually as follows:
Select Maintenance and press Enter.
Select Backup and press Enter.
Select Incremental Backup and press Enter (see Fig. 7.60).
→ A message informs that the backup was started in the background.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
7.3.2.2 Restoring a Backup Manually¶
Note
Only backups created with the currently used GOS version or the previous GOS version can be restored. For GOS 21.04, only backups from GOS 20.08 or GOS 21.04 can be imported. If an older backup should be imported, e.g., from GOS 5 or GOS 6, an appliance with a matching GOS version has to be used.
Backups created with GOS versions newer than the currently used GOS version are also not supported. If a newer backup should be imported, an appliance with a matching GOS version must be used.
Only backups created with the same appliance model (see Chapter 3) can be restored.
It is checked whether the subscription keys of the backup and the appliance to which the backup should be restored are identical. If the keys do not match, a warning is displayed and the user must confirm that the key on the appliance should be overwritten. However, if a backup without a subscription key is restored, the key on the appliance is kept.
If there are any questions, contact the Greenbone Enterprise Support.
A backup can be restored as follows:
Select Maintenance and press Enter.
Select Backup and press Enter.
Select List and press Enter.
Select the desired backup and press Enter.
Select Yes and press Enter if both user data and system settings should be uploaded.
or
Select No and press Enter if only user data should be uploaded.
Note
The system settings include all GOS configurations, e.g., the network settings. The data includes all vulnerability scanning and vulnerability management information.
→ A warning informs that all local settings are lost if the backup is restored (see Fig. 7.61).
Confirm the message by selecting Yes and pressing Enter.
→ A message informs that the restoration was started in the background.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
7.3.2.3 Performing a Backup Using a USB Stick¶
Backups can be transferred to a USB stick as follows:
Connect a USB stick to the appliance.
Note
A FAT-formatted USB stick has to be used. In case of problems, another USB stick or another USB port on the appliance should be tried.
Select Maintenance and press Enter.
Select Backup and press Enter.
Select USB Backup and press Enter.
Select Backup and press Enter (see Fig. 7.62).
→ A message asks to confirm the backup.
Select Yes and press Enter.
→ A message informs that the backup was started in the background.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
7.3.2.4 Restoring a Backup Using a USB Stick¶
Note
Only backups created with the currently used GOS version or the previous GOS version can be restored. For GOS 21.04, only backups from GOS 20.08 or GOS 21.04 can be imported. If an older backup should be imported, e.g., from GOS 5 or GOS 6, an appliance with a matching GOS version has to be used.
Backups created with GOS versions newer than the currently used GOS version are also not supported. If a newer backup should be imported, an appliance with a matching GOS version must be used.
Only backups created with the same appliance model (see Chapter 3) can be restored.
It is checked whether the subscription keys of the backup and the appliance to which the backup should be restored are identical. If the keys do not match, a warning is displayed and the user must confirm that the key on the appliance should be overwritten. However, if a backup without a subscription key is restored, the key on the appliance is kept.
If there are any questions, contact the Greenbone Enterprise Support.
Backups can be restored from a USB stick as follows:
Connect a USB stick to the appliance.
Note
A FAT-formatted USB stick has to be used. In case of problems, another USB stick or another USB port on the appliance should be tried.
Select Maintenance and press Enter.
Select Backup and press Enter.
Select USB Backup and press Enter.
Select Restore and press Enter (see Fig. 7.62).
Select Yes and press Enter if both user data and system settings should be uploaded.
or
Select No and press Enter if only user data should be uploaded.
Note
The system settings include all GOS configurations, e.g., the network settings. The data includes all vulnerability scanning and vulnerability management information.
→ A warning informs that all local settings are lost if the backup is restored (see Fig. 7.63).
Confirm the message by selecting Yes and pressing Enter.
→ A message informs that the restoration was started in the background.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
7.3.3 Copying Data and Settings to Another Appliance with Beaming¶
The current state of an appliance can be copied to another appliance. This includes user data (e.g., tasks, reports, results) and system settings, i.e., the GOS configuration.
On the receiving appliance, the user can decide whether to import only the user data, or both the user data and the system settings.
Note
Only beaming images created with the currently used GOS version or the previous GOS version can be restored. For GOS 21.04, only beaming images from GOS 20.08 or GOS 21.04 can be imported.
It is only possible to import a beaming image to an appliance if the release information, i.e., the list of available GOS upgrades, on the corresponding appliance is up-to-date. To ensure this, a current Greenbone Enterprise Feed should be downloaded.
Beaming images created with GOS versions newer than the currently used GOS version are also not supported. If a newer beaming image should be imported, an appliance with a matching GOS version must be used.
Beaming is only allowed to an appliance of the same or of a higher class (see Chapter 3). Beaming to a Greenbone Enterprise TRIAL is not supported.
It is checked whether the subscription keys of the beaming image and the appliance to which the beaming image should be restored are identical. If the keys do not match, a warning is displayed and the user must confirm that the key on the appliance should be overwritten. However, if a beaming image without a subscription key is restored, the key on the appliance is kept.
If there are any questions, contact the Greenbone Enterprise Support.
7.3.3.1 Beaming Directly from Another Appliance¶
The beaming image can be created and copied directly as follows:
Note
- Appliance A = Sending appliance
- Appliance B = Receiving appliance
In the GOS administration menu of Appliance A, select Maintenance and press Enter.
Select Beaming and press Enter.
Select Download and press Enter (see Fig. 7.64).
→ A message informs that the beaming image creation was started in the background.
When the creation is finished, a message informs that a password that has to be noted will be shown.
Press Enter.
Note the password. It is needed in step 13.
Press q to close the editor.
Important
Do not close the message displaying the URL.
In the GOS administration menu of Appliance B, select Maintenance and press Enter.
Select Beaming and press Enter.
Select Upload from GSM A and press Enter.
Enter the URL displayed in the GOS administration menu of Appliance A in the input box and press Enter.
Select Yes and press Enter if both user data and system settings should be uploaded.
or
Select No and press Enter if only user data should be uploaded.
→ A warning asks to confirm the process.
Select Yes and press Enter.
Enter the password from step 5 in the input box and press Enter (see Fig. 7.66).
→ A message informs that the beaming image upload was started in the background.
When the upload is finished, a message is displayed.
Press Enter.
7.3.3.2 Beaming via Remote File System¶
A beaming image can be created, downloaded, stored, and imported later via a remote file system as follows:
Note
- Appliance A = Sending appliance
- Appliance B = Receiving appliance
In the GOS administration menu of Appliance A, select Maintenance and press Enter.
Select Beaming and press Enter.
Select Download and press Enter (see Fig. 7.67).
→ A message informs that the beaming image creation was started in the background.
When the creation is finished, a message informs that a password that has to be noted will be shown.
Press Enter.
Note the password. It is needed in step 16.
Press q to close the editor.
Open the web browser and enter the displayed URL.
Download the GSMB file.
In the GOS administration menu of Appliance B, select Maintenance and press Enter.
Select Beaming and press Enter.
Select Upload via remote file system and press Enter.
Open the web browser and enter the displayed URL.
Click Browse…, select the GSMB file and click Upload.
Select Yes and press Enter if both user data and system settings should be uploaded.
or
Select No and press Enter if only user data should be uploaded.
→ A warning asks to confirm the process.
Select Yes and press Enter.
Enter the password from step 5 in the input box and press Enter (see Fig. 7.69).
→ A message informs that the beaming image upload was started in the background.
When the upload is finished, a message is displayed.
Press Enter.
7.3.4 Performing a GOS Upgrade¶
During the daily feed update at maintenance time (see Chapter 7.2.13), the appliance will also download new GOS upgrades if available. While the upgrades are automatically downloaded, they are not automatically installed.
Note
Since the upgrades might interrupt current scan tasks, they need to be scheduled carefully.
Upgrades can be installed manually as follows:
Select Maintenance and press Enter.
Select Upgrade and press Enter.
Select Upgrade and press Enter to install an upgrade.
or
Select Switch Release and press Enter to switch to a new release.
→ A message informs that the upgrade was started in the background.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
Note
If errors occur when using the web interface after a GOS upgrade, the browser or page cache must be cleared (see Chapter 6.4).
It is possible that a GOS upgrade changes the functionality available via the GOS administration menu. This changed functionality will only be available after reloading the GOS administration menu. Therefore, it is recommended to log out of the GOS administration menu and log back in after the GOS upgrade.
Occasionally, a reboot of the appliance is required as well (see Chapter 7.3.9.1). The self-check shows an according note if this is the case (see Chapter 7.3.1).
Note
By default, a successful GOS upgrade on the master starts a GOS upgrade on connected sensors as well. Nonetheless, an upgrade can manually be installed on sensors (see Chapter 7.3.5).
7.3.5 Performing a GOS Upgrade on Sensors¶
A GOS upgrade on a sensor can be installed as follows:
Select Maintenance and press Enter.
Select Upgrade and press Enter.
Select Sensors and press Enter.
Select the desired sensor and press Space.
→ The sensor is marked with *. Multiple sensors can be selected at the same time.
Sensors that are not ready for an upgrade are labelled accordingly.
Press Enter.
→ A message informs that the upgrade was started in the background.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
7.3.6 Performing a Feed Update¶
By default, the appliance will try to download feed updates and GOS upgrades daily at its maintenance time (see Chapter 7.2.13).
Additionally, a feed update can be triggered manually as follows:
Select Maintenance and press Enter.
Select Feed and press Enter.
Select Update and press Enter (see Fig. 7.70).
→ A message informs that the feed update was started in the background.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
Note
By default, a successful feed update on the master starts a feed update on connected sensors as well. Nonetheless, a feed update can manually be pushed to sensors (see Chapter 7.3.7).
7.3.7 Performing a Feed Update on Sensors¶
A feed update can be pushed to a sensor as follows:
Select Maintenance and press Enter.
Select Feed and press Enter.
Select Sensors and press Enter.
Select the desired sensor and press Enter (see Fig. 7.71).
→ A message informs that the feed update was started in the background.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
7.3.8 Upgrading the Flash Partition¶
The flash partition is used to perform factory resets of the appliance. To make factory resets easier, it should be upgraded to the latest GOS version.
Note
Make sure the appliance itself is able to establish a connection to the Greenbone Feed Server.
It is not possible to upgrade the flash partition of sensors via the master.
The flash partition can be upgraded as follows:
Upgrade the appliance to the latest GOS version (see Chapter 7.3.4).
Select Maintenance and press Enter.
Select Flash and press Enter.
Select Download and press Enter (see Fig. 7.72).
→ The latest flash image is downloaded.
Tip
The download status can be monitored in the live logs (Advanced > Logs > Live, see Chapter 7.4.1).
When the download is finished, select Write and press Enter (see Fig. 7.72) .
→ The image is written to the flash partition. The process may take up to 20 minutes.
Tip
The currently running system operation can be displayed by selecting About and pressing Enter in the GOS administration menu.
7.3.9 Shutting down and Rebooting the Appliance¶
Important
The appliance should not be turned off using the power switch.
The appliance should be shut down and rebooted using the GOS administration menu instead. This ensures that mandatory cleanup processes are run during the shutdown and reboot.
7.3.9.1 Rebooting the Appliance¶
The appliance is rebooted as follows:
Select Maintenance and press Enter.
Select Power and press Enter.
Select Reboot and press Enter.
→ A message asks to confirm the reboot (see Fig. 7.73).
Select Yes and press Enter.
→ The appliance will reboot. The reboot process may take up to several minutes.
7.3.9.2 Shutting down the Appliance¶
The appliance is shut down as follows:
Select Maintenance and press Enter.
Select Power and press Enter.
Select Shutdown and press Enter.
→ A message asks to confirm the shutdown (see Fig. 7.74).
Select Yes and press Enter.
→ The appliance will shutdown. The shutdown process may take up to several minutes.
7.4 Advanced Menu¶
7.4.1 Displaying Log Files of the Appliance¶
The log files of the appliance can be displayed as follows:
Select Advanced and press Enter.
Select Logs and press Enter.
Select the desired logs and press Enter (see Fig. 7.75).
→ The log file is displayed in a viewer.
Press q or Ctrl + C to quit the viewer.
7.4.2 Performing Advanced Administrative Work¶
7.4.2.1 Managing the Superuser Account¶
When the shell is accessed, a Linux command line as the unprivileged user admin is displayed (see Chapter 7.4.2.3). Any Linux command can be executed.
Note
The privileged account root (superuser) should only be used in consultation with the Greenbone Enterprise Support.
If any modifications are done without consultation, the entitlement to receive assistance by the Greenbone Enterprise Support expires.
To obtain root privileges on the appliance, the command su - has to be entered in the shell.
Using su - to switch from the admin user to the root user is disabled by default.
The superuser has to be enabled and provided with a password as follows:
Select Advanced and press Enter.
Select Support and press Enter.
Select Superuser and press Enter.
Select Superuser State and press Enter (see Fig. 7.76).
→ A warning informs that root privileges should only be obtained by exception and while consulting the Greenbone Enterprise Support.
Select Yes and press Enter.
→ A message informs that the changes have to be saved (see Chapter 7.1.3).
Press Enter to close the message.
Select Password and press Enter.
Enter the password twice, select OK and press Enter (see Fig. 7.77).
7.4.2.2 Generating and Downloading a Support Package¶
Sometimes the Greenbone Enterprise Support requires additional information to troubleshoot and support customers. The required data is collected as an (encrypted) support package including all configuration data of the appliance.
The package can be encrypted using the GPG public key of the Greenbone Enterprise Support. The support package is stored on the appliance.
A support package can be created as follows:
Select Advanced and press Enter.
Select Support and press Enter.
Select Support Package and press Enter.
→ A message asks to confirm the generation of the support package.
Select Yes and press Enter.
→ A message asks whether the support package should be encrypted (see Fig. 7.78).
Select Yes and press Enter to encrypt the support package.
or
- Select No and press Enter to not encrypt the support package.
If an encrypted support package was chosen, open the web browser, enter the displayed URL and download the GPG file (encrypted ZIP folder).
or
Note
If the support package is not encrypted, the download needs to be done using the Secure Copy Protocol (SCP). For this, SSH has to be enabled first (see Chapter 7.2.4.4).
If an unencrypted support package was chosen, enter the displayed command using SCP (see Fig. 7.79) and download the support package (ZIP folder).
Note
The “.” at the end can be replaced with a path. If the “.” is maintained, the current folder is chosen.
Send the ZIP folder to the Greenbone Enterprise Support.
On Microsoft Windows systems the support package can be downloaded using either pscp, a command line tool included in PuTTY, or smarTTY, a graphical tool implementing SCP.
7.4.2.3 Accessing the Shell¶
Shell access is not required for any administrative work, but may be requested by Greenbone Enterprise Support for diagnostics and support.
The shell can be accessed as follows:
Select Advanced and press Enter.
Select Support and press Enter.
Select Shell and press Enter.
→ A warning informs that the shell level is undocumented and should not be used for administrative settings (see Fig. 7.80).
Select Continue and press Enter.
→ A Linux shell is opened using the unprivileged user admin (see Fig. 7.81).
Note
Accessing as root requires the enabling of the superuser and the determination of a password (see Chapter 7.4.2.1). Afterwards, switching to root using the command
su -is possible.Enter
exitor press Ctrl + D to quit the shell.
7.4.3 Displaying the Greenbone Enterprise Feed Subscription Key¶
The subscription key (see Chapter 7.2.7.1) can be displayed as follows:
Select Advanced and press Enter.
Select Subscription and press Enter (see Fig. 7.82).
→ The subscription key is displayed in a viewer.
Press q to quit the viewer.
7.5 Displaying Information about the Appliance¶
Information about the appliance can be displayed by selecting About and pressing Enter.
The following information is displayed:
- Appliance model
- GOS version
- Feed version
- Name of the subscription key
- IP address of the web interface
- Configured sensors
- Currently running system operations

 English |
English |